In the spring, Netwrix conducted a survey designed to identify IT security, compliance and operations risks that organizations around the globe face on the daily basis. The findings of the survey are summarized in our 2017 IT Risks Report.
This series of blog posts dives deeper into the data we collected for various industries. In previous posts, we analyzed the results for the healthcare and financial verticals. This time, we’ll focus on feedback provided by government entities.
We know that cyber attacks are becoming more sophisticated and intense. We also know that some attackers are very interested in the sensitive data stored by government agencies — from citizens’ data (addresses, driver’s license numbers, Social Security numbers, financial data, healthcare records and) to other information critical to local or national security. Other adversaries are more interested in gaining access to critical infrastructures in order to damage control systems or disrupt public services. Finally, we know that government entities are required to comply with various data protection regulations.
How do government entities keep up? Let’s look at our findings.
Who is seen as the main threat?
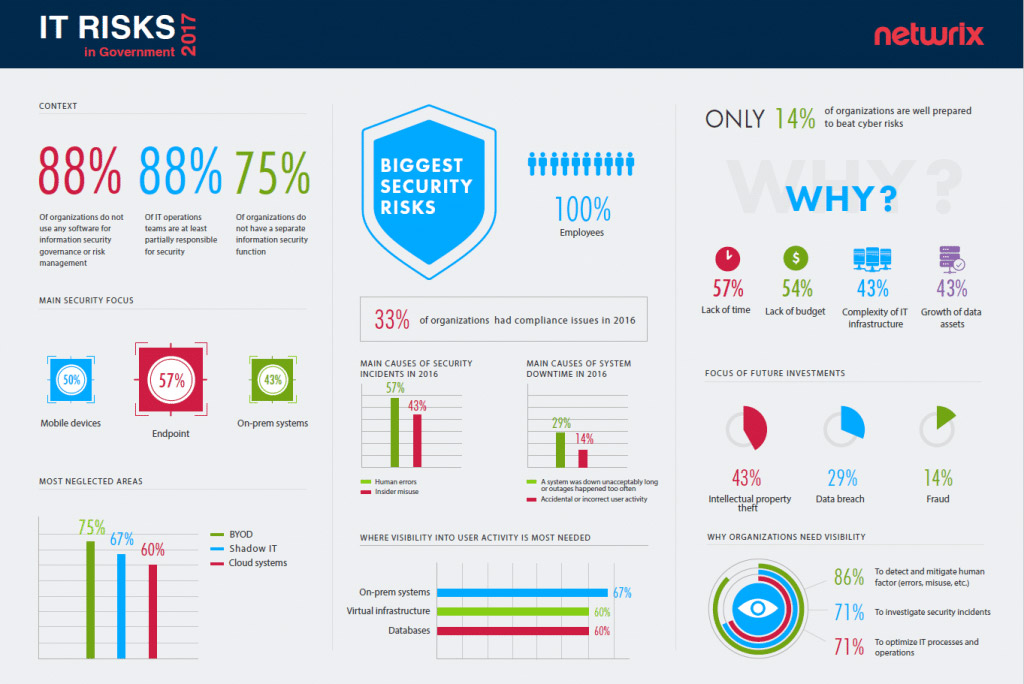
All government entities surveyed consider their own employees to pose the biggest threat. It is interesting how the loudest headlines (state-sponsored attacks carried out by hackers, for example) don’t always correspond with the respondents’ perceptions and priorities.
100% of government entities see their own employees as the biggest threat to security
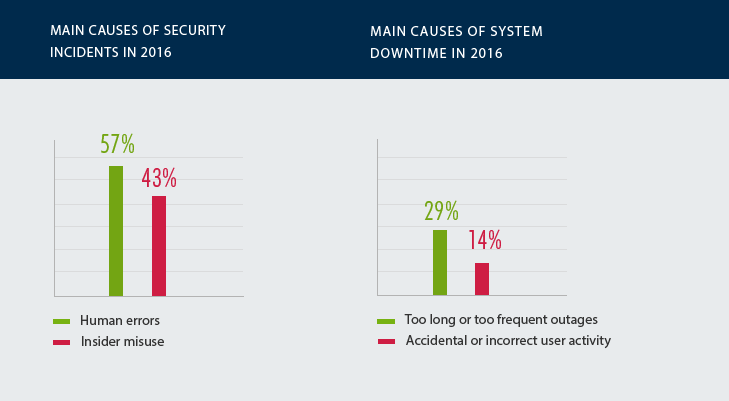
So, why do government entities have little trust in their own employees? The main reason is bad experiences. In 2016, human errors caused security incidents in 57% of government entities and system downtime in 14% of them. In addition, 43% of organizations admitted they had to investigate security incidents that involved insider misuse.
What resources are being used to combat the threat?
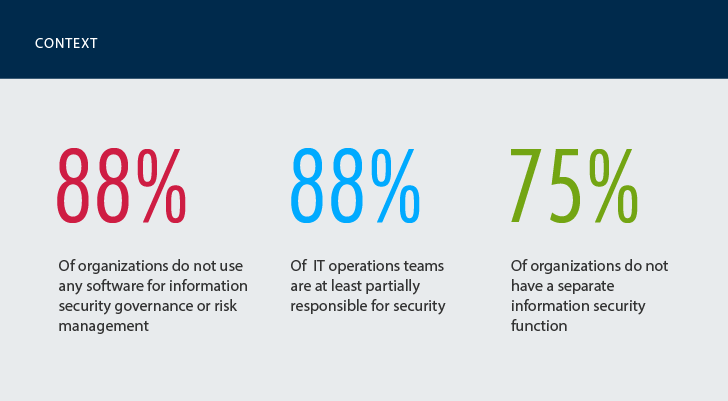
The majority of government organizations have not implemented security governance or risk management within their IT infrastructures. About three-quarters of respondents said there are no dedicated security personnel in their organizations. This means that compliance, just like security, is shouldered by IT operations teams.
75% of government entities do not have a separate information security function
As a result, IT operations are overloaded with dissimilar tasks and struggle to be efficient and proactive everywhere. No wonder so many junior and middle IT staff complained about lack of time (57%) and lack of budget (54%) as the main factors preventing them from taking a more serious approach to security.
What has been done to mitigate cybersecurity risks?
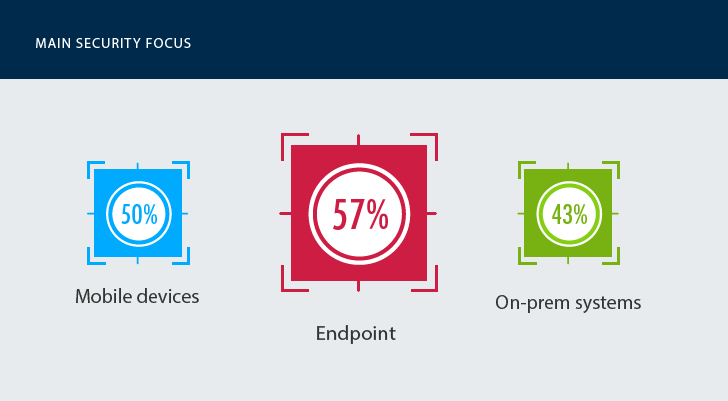
Given that context, what have government entities managed to achieve in the area of cyber security? Not much, as expected. They focus on protecting endpoints (57%), corporate mobile devices (50%) and on-premises systems (43%) — even as the threat landscape and the modern IT infrastructure has changed.
57% of government entities have been focusing their security efforts on protecting endpoints, rather than data
Government entities are lagging behind in understanding what is happening beyond the traditional perimeter. The majority of respondents have zero visibility into BYOD, shadow IT and cloud systems. Visibility into user activity across the IT infrastructure is not very common: Only 38% of respondents claim to be well aware of the activity of users, IT admins and third parties with legitimate access to internal systems. This is extremely strange considering the fear of malicious insiders that all of the respondents expressed. Moreover, one would think that if government entities don’t track all user activity, at least they would know what is happening with their data. Sadly, the data-centric approach is not popular either. Only four in ten organizations thoroughly monitor activity in databases, though 60% of the respondents deem it critical.
The data breaches at the IRS, Navy and Office of Personnel Management seem like logical consequences of this general lack of awareness concerning both user activity and data manipulations.
Why is visibility into user activity across the IT infrastructure so critical?
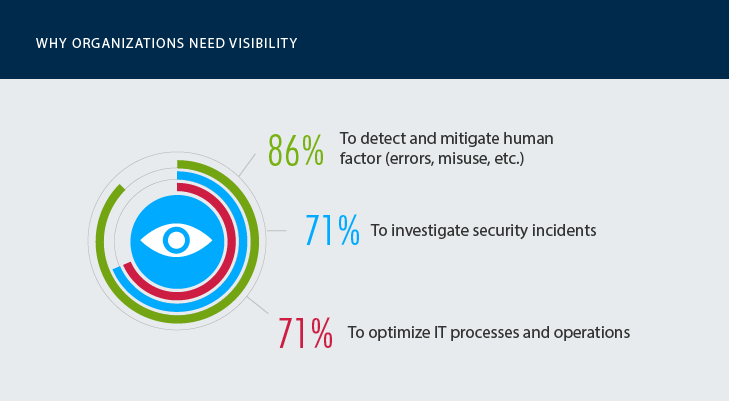
We asked government agencies to name the main benefits they gain from deeper visibility into user activity in at least some systems. 86% of respondents said it helps them detect and mitigate human factor risks, both honest mistakes and malicious actions. About 71% of organizations cited quicker investigation of security incidents and optimization of IT processes.
Fragmented visibility is better than no visibility at all; 86% of government entities say it helps them better detect human factor risks
The latter is another interesting finding, because it confirms that organizations are still struggling to optimize IT operations. But given our earlier finding that few organizations have dedicated security staff, it will come as no surprise that IT operations teams simply do not have time to build security strategy, conduct regular employee training, research cyber security developments, or anything else that falls into the “taking a proactive approach” category. Organizations mostly remain in reactive mode, which is not a perfect setup, since most of them do not have sufficient visibility into activity in many parts of their IT infrastructures.
Lack of visibility into user activity across critical systems can lead not only to security incidents and system downtime, but also to failed IT audits. Given the generally poor level of security and lack of user activity monitoring, it is surprising that only 33% of government entities had trouble passing a compliance audit in 2016.
Is IT security likely to improve at government agencies?
Only 14% of government organizations consider themselves to be well protected against threats. They cite a variety of reasons, from the lack of time (57%) and budget (54%) to the growing complexity of IT infrastructure (43%) and data assets (43%). Given that each entity always names a combination of reasons, it is unlikely the bigger security and compliance picture will change dramatically in the near future.
86% of government entities are not well prepared for cyber attacks
The general conclusion we can draw is that government agencies need to start approaching IT risk from the top down: Senior management must get more deeply involve and fund cyber-security initiatives. Otherwise, their IT teamss will not have the visibility required to maintain stable IT operations, comply with regulatory requirements and identify ongoing security threats, let alone proactive risk mitigation.
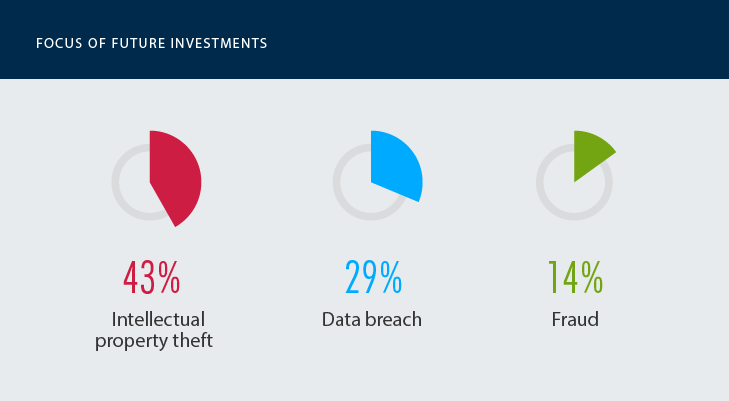
Many of their IT pros do recognize the immediate and long-term value of gaining deeper visibility into activity across the IT infrastructure. If they are provided with the right support, human resources and proper analytics, we will quickly see improvements and at some point, data breaches at government agencies will disappear from the headlines.
View the full infographics (click on the image to open a high-resolution version in a new tab)
Interested in learning about other findings from this survey? Please read the full Netwrix 2017 IT Risks Report

.png)