- Home
- Security, Compliance, and Identity
- Core Infrastructure and Security Blog
- How to Manage Microsoft Defender Policies with Intune on Non-Managed Devices
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Architecture and Capabilities:
From the endpoint security management architecture perspective, this scenario fulfills the gap of managing endpoint security features on unmanaged devices. For Intune managed devices, either cloud-only or co-management scenarios provided the endpoint security management capabilities. Also, Intune and Configuration Manager integration provided similar management capabilities for on-prem (ConfigMgr) managed devices.
Finally, security configuration enforcement integration between MDE and Intune helps security teams to use the same admin interface – Intune console – to deploy Security policies to the devices that are enrolled to MDE only.

So let’s have a look at the configuration requirements and components of the solution first and start configuring on our test tenant and validate the configuration afterwards:
First, supported platforms while this document was written were Windows Server operating systems starting from Windows Server 2012 R2 up to Windows Server 2022 and Windows 1x clients. However it is always a good idea to check the official documentation for an updated list of supported platforms.
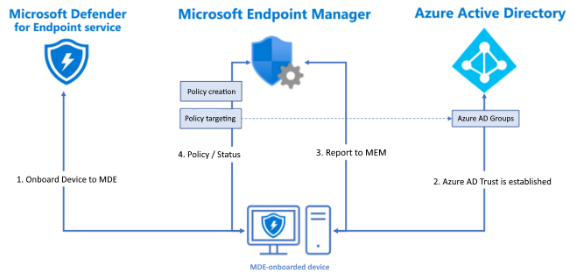
Conceptually, devices need to be enrolled to Microsoft Defender for Endpoint service to be able to have policies applied. Also, an Azure AD trust is required to communicate with AAD & Intune. Once communication is started with Intune, status is reported, and policy information is pushed down and applied to the endpoint.
From capabilities perspective, Intune – MDE integration provides fundamental security policy management such as antivirus configuration, antivirus exclusions, firewall configuration, firewall configuration exclusions and EDR configuration. However, it is always a good idea to check for updated capability documentation to check for future capability improvements while making a decision.
Initial Status:
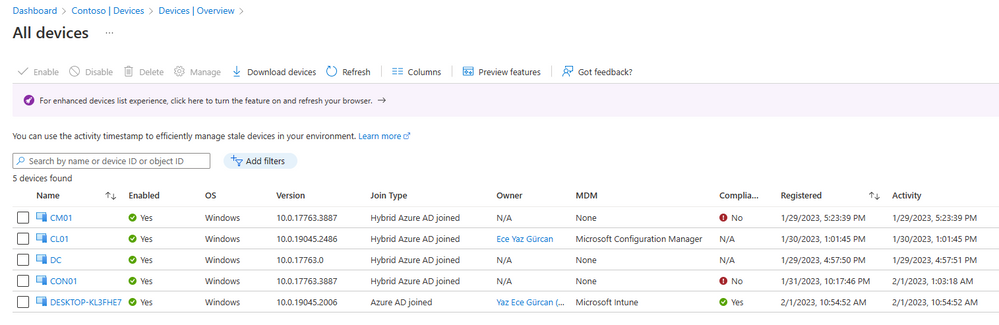
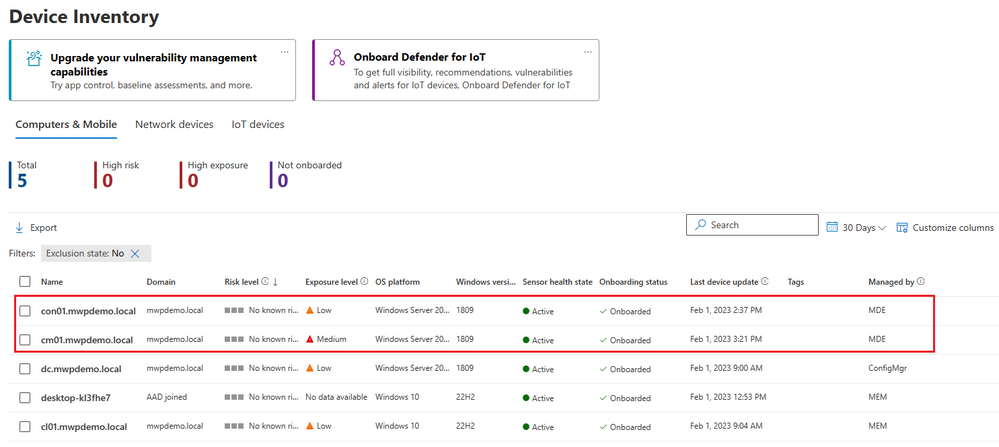
I have started configuration by onboarding several devices to MDE tenant. As you can see from the device inventory view in MDE; two of them are managed directly by Intune (MEM), one of them is managed by Configuration Manager agent and a two listed as “Unknown” in managed by column.

Configuration management view also shows the same information focused on Security Enforcement feature in graph view. As you can see from the following snippet, no devices security settings are enforced by MDE in the initial status.

When looking at the Endpoint Manager console for all devices, we would see only the ones that are managed are listed:

Also, on the Azure AD portal we can see the devices that are already joined to the tenant. Note that not all of the AAD Joined devices are listed in Intune.
Now let's proceed with the integration.
Configuring the Integration
Integration has two parts in configuration. First part is to integrate Microsoft Defender for Endpoint and Microsoft Intune if not already integrated. This is done in Settings – Endpoints – Advanced Features view. When scrolled through the available features, Microsoft Intune connection can be seen. Once it is turned on, it will also be available on the Intune side.

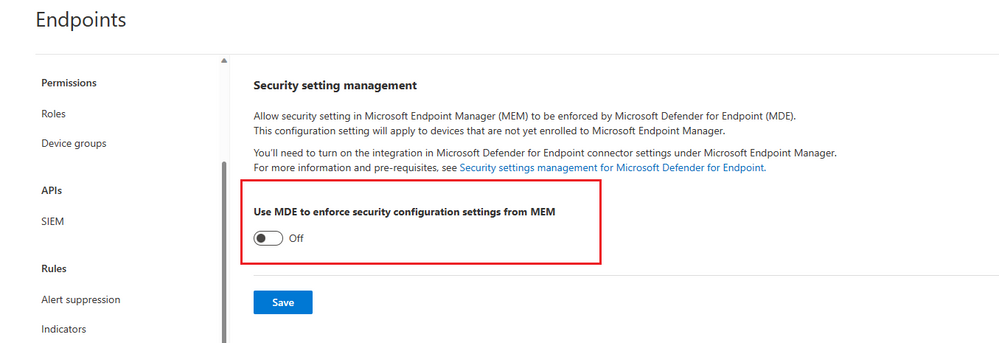
Second, configuration is about Security settings management. This configuration can be turned on from Settings – Endpoints – Configuration Management.
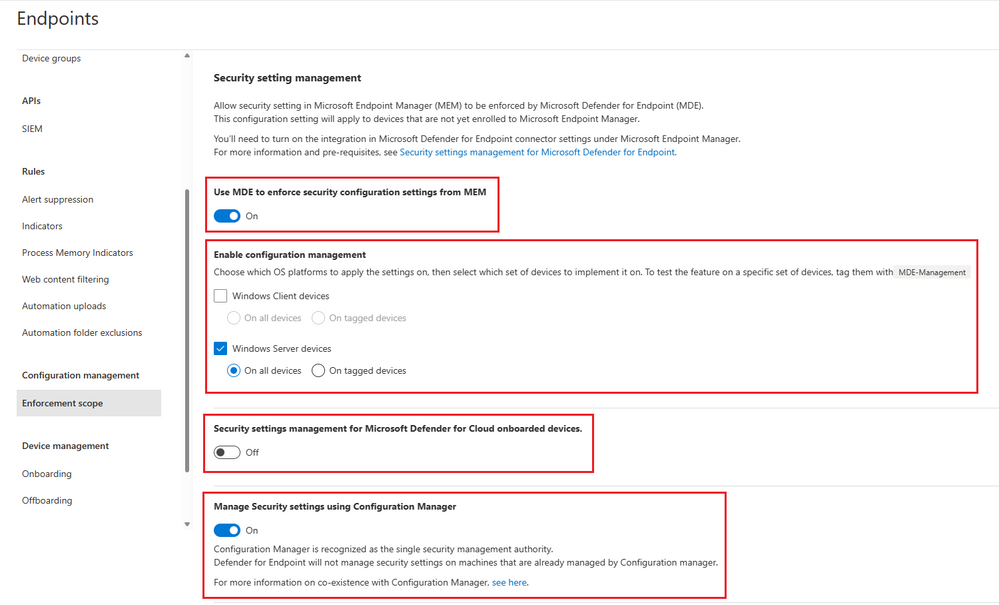
When turned on, additional configuration options will be available to define enforcement scope for endpoint security configuration.
The first option is selecting windows device type for configuration enforcement. We can distinguish between Windows client and Windows Server devices. Also, it is possible to define a subset of these device types by tagging them as “MDE-Management” so that a more granular management would be in place.
The second section defines if the security settings management for devices that are enrolled by Microsoft Defender for Cloud will be handled by MDE.
The last option is to define the enforcement for the devices that have Configuration Manager agent. With this setting turned on, configuration manager agent will take care of security policies on CM managed devices.
These settings were the ones that allow MDE to push down the security policies created in Intune. However, a simpler configuration is also needed on Intune end to enable MDE integration. This configuration is present in Microsoft Defender for Endpoint view under Endpoint security node.
Setting is listed as “Allow Microsoft Defender for Endpoint to enforce Endpoint Security Configurations”. Once this setting is turned on, it will open MDE channel for pushing down the security policies.
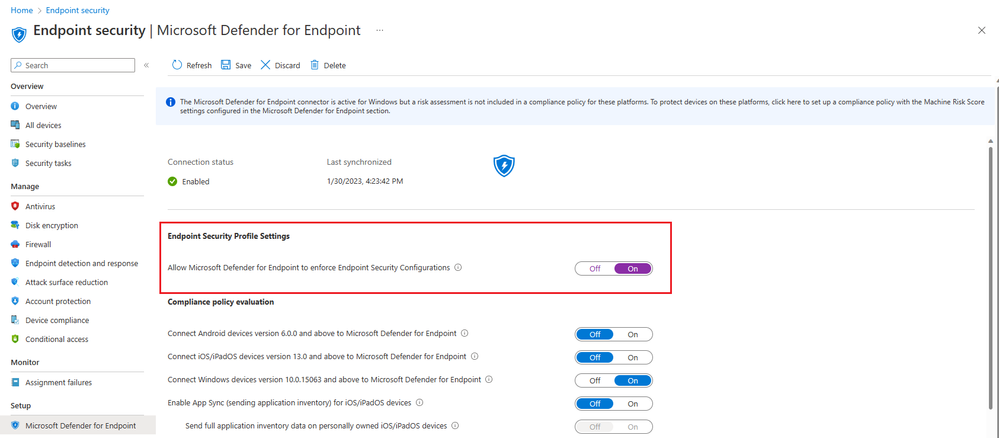
Post Configuration:
First change following the configuration is the new reflected device to Microsoft Intune. As you can see new device named CON01 is reflected on Intune console. Its management authority is listed as MDE.

On Microsoft Defender for Endpoint, we can see the managed by attribute for devices that was reported as “Unknown” turns to “MDE” under device inventory.
It is also reflected in the configuration management section. Following our configuration, 40% of devices security settings are enforced by MDE. Device configuration management view also gives information about devices that are onboarded via MDE security management feature.

I won’t go into the specifics of the AV policies that you may configure via Intune, however when you take a look at a policy that is created in the Intune console, you may see the target policy applies is listed as mdm and microsoftSense. Meaning this policy is applied on Intune managed devices as well as devices that have security enforcement is configured for MDE.

Controls in Client:
After you validate that the security configuration is enforced to the client from MDE console, there are two main controls on the client side to make sure the policies are applied. The first thing to check is the Windows Security application itself. You will notice that Virus & threat protection settings are listed as managed by system administrator and is configured by the policy settings created in Intune.

Second control would be running a “get-mppreference” commandlet on the endpoint. It will show the running policy configuration on the endpoint.

Things to Consider:
Azure AD Trust: For the integration to work properly, all devices should have some trust relationship with Azure AD. When you consider Domain Joined devices; this would be Hybrid Azure AD Joining the devices. On the other hand, Domain Controller devices are not capable of doing a Hybrid Azure AD Join - at least that was the case while this post is written. So, if you will need to manage Microsoft Defender in your DCs, you will either need a Configuration Manager integration as discussed here, or you will need to have a legacy solution such as GPOs for this specific server role.
OS Upgrade Level: Most companies have a better level of update than my lab environment. And i found it in the hard way that the OS Update level can be a problem while waiting for things to work. My bad that i've used vanilla versions of WS 2019, which is already 3 years old. Bottomline, check if your devices are in the supported OS level.
Creating Groups for Policies: I did not walk through the process, however if you need to apply different AV configurations for different device types, it would be a good idea to create groups and apply policies to those groups as detailed here.
Tamper Protection: Another interesting learning for me is the fact that you will need to disable tamper protection before applying these policies. Otherwise, it won't work as mentioned here.
Wrap-up
Intune has an integration with Microsoft Defender for Endpoint which allows fundamental security policy enforcement on non-managed clients. Even though this is limited to Antivirus, Firewall and EDR policies; it fills an important gap on certain scenarios. This also helps Intune to be a unified endpoint security management interface for companies.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.