- Home
- Microsoft Intune and Configuration Manager
- Intune Customer Success
- Announcing Windows LAPS management through Microsoft Intune
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Every single Windows device has a built-in local administrator account. It's required, can’t be deleted, and, given its high privileges, has full access to the device. This local admin account is protected by its account password, which means that enterprises have no choice but to make sure the password is continuously secured and protected to avoid vulnerability attacks and security breaches. Many customers use the stand-alone, on-premises product called Windows Local Admin Password Solution (LAPS) for password management. Although widely adopted, the LAPS solution didn’t support local admin password management in the cloud, until now.
Intune is excited to announce the ability to manage and support Windows LAPS, bringing Microsoft’s admin password management solution to the cloud.
Windows LAPS has been revamped to integrate into the Windows platform to securely rotate and backup passwords using Microsoft Entra, Azure Active Directory (Azure AD). IT admins can use the first-class management experiences built into Intune to configure Windows LAPS and leverage the capabilities that are now available.
To learn more about the Windows LAPS implementation, see Windows LAPS overview | Microsoft Learn.
Pre-requisites
To use Windows LAPS in Intune, ensure you’re using a supported Windows platform:
- Windows 10 20H2 and later with April 11, 2023 security updates installed
- Windows 11 21H2 and later with April 11, 2023 security updates installed
- Windows Server 2019 and later with April 11, 2023 security updates installed
For more information, read: By popular demand: Windows LAPS available now!
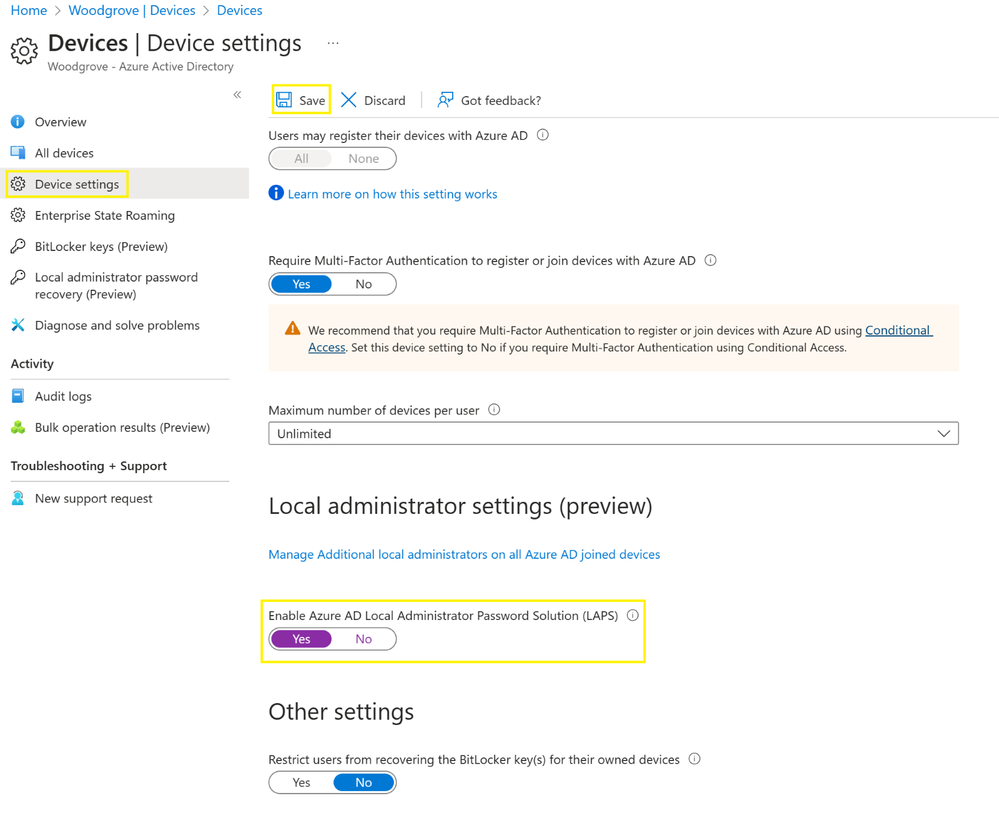
Enable Windows LAPS in Azure AD
To use Windows LAPS, you will need to enable it for Azure AD devices in the Microsoft Azure portal. Navigate to Azure Active Directory > Devices > Device settings, under Local administrator settings (preview), select Yes for "Enable Azure AD Local Administrator Password Solution (LAPS)" and click Save.
Walkthrough
Let’s take a look at the experiences available with Intune to manage Windows LAPS. For a demonstration of the admin experience described in this blog, watch this video: https://aka.ms/Intune/Windows-LAPS-video
Managing Windows LAPS policies with Intune
Admins can configure Windows LAPS settings through the dedicated policy template found in the Microsoft Intune admin center > Endpoint security > Account protection > Windows 10 and Later > Local admin password solution (Windows LAPS) (preview). From there, settings taken from the LAPS configuration service provider (CSP) are available for configuration.
Admins can choose which directory to back up the password to (Azure AD or Active Directory), which will dictate the available configuration settings. Admins can configure settings related to password complexity and length, as well as specify the admin account name and behavior for post authentication actions.


Once complete, admins can target the policy to their Azure AD groups and view the success or errors through Intune’s policy reporting experience. Permissions to create or manage the Windows LAPS policy follow suit with the Security baseline permissions that are applicable to all policy templates in Endpoint security.
Note, if you're choosing between different types of policies, the more restrictive one will take precedence over others. Specifically, the order of precedence is MDM > GPO > Local > Legacy LAPS.
Viewing the local admin password for a specific device
Admins can select a specific device (Devices > All devices) and have the option to view the local admin password for the selected device. They can select the option under Monitor > Local admin password, which will surface the same information also available through the Azure portal. With the right permissions, admins can view the metadata related to the device’s password schedule (last rotation, next rotation, account name) and, with appropriate permissions, retrieve the current local admin password by selecting the Show button.

If admins don’t have the correct permissions, they won’t be able to view the relevant information. This information is controlled by the deviceLocalCredentials.Read.All permissions that are specific to Global Admin, Cloud Device Admin, and Intune Admin, which only allows them to recover the Windows LAPS password.
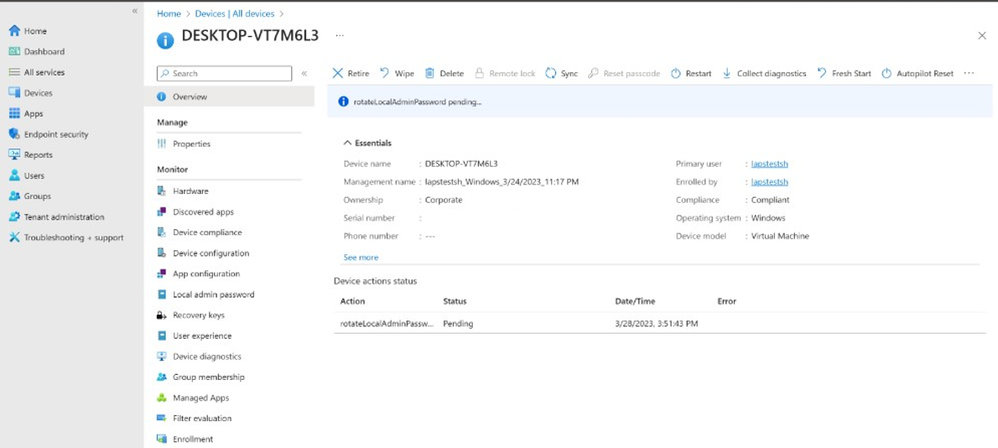
Using device actions to rotate a local admin password
If an admin wishes to rotate the local admin password outside of the schedule rotation interval, they can leverage the Intune device action framework. By selecting a supported device, the option to Rotate local admin password is available and can be initiated. This will trigger a device action, which shows the status to the admin on the Device page. Once complete, the rotation timestamp will update, and the new password will be available. Note, this is only applicable to devices that have Windows LAPS policies targeted to them and have the backup directory set to Active Directory or Azure AD. If not supported on the device, this will return as an error.

This capability is controlled by the new Remote tasks > Rotate local admin password permission found through Intune tenant administration.

Audit logs
Admins can use Azure AD audit logs to view auditing events related to managing the local admin password. See Audit logs in Azure Active Directory to learn more.
To learn more about the capabilities of Windows LAPS, see:
- Microsoft Intune support for Windows LAPS | Microsoft Learn
- Manage Windows LAPS policy with Microsoft Intune | Microsoft Learn
- Reports for LAPS policy in Intune | Microsoft Learn
-
By popular demand: Windows LAPS available now! | Windows IT Pro Blog
Let us know what you think by leaving a comment below or reaching out to us on Twitter @IntuneSuppTeam.
Updates
4/28/2023: Updated to include how to enable Windows LAPS in Azure AD.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.