- Home
- Microsoft Intune and Configuration Manager
- Intune Customer Success
- New settings in Microsoft Intune to enhance Windows Defender Firewall management
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
We're pleased to highlight some of the new additions made to the Microsoft Intune admin center to configure settings related to Windows Defender Firewall. Admins can take advantage of these capabilities to enhance security and ease Defender Firewall management. The properties come directly from the Firewall configuration service provider (CSP) and apply to the Windows platform.
The following settings can be configured through the Intune admin center under Endpoint security > Firewall. Policy templates can be found via Create policy > Windows 10, Windows 11, and Windows Server > Microsoft Defender Firewall or Microsoft Defender Firewall Rules.
Note, devices using the Security Management for Microsoft Defender for Endpoint attach solution will report as Not Applicable as the following settings aren’t currently supported with this capability.
WDAC Application ID Tagging with Intune Firewall Rules policy
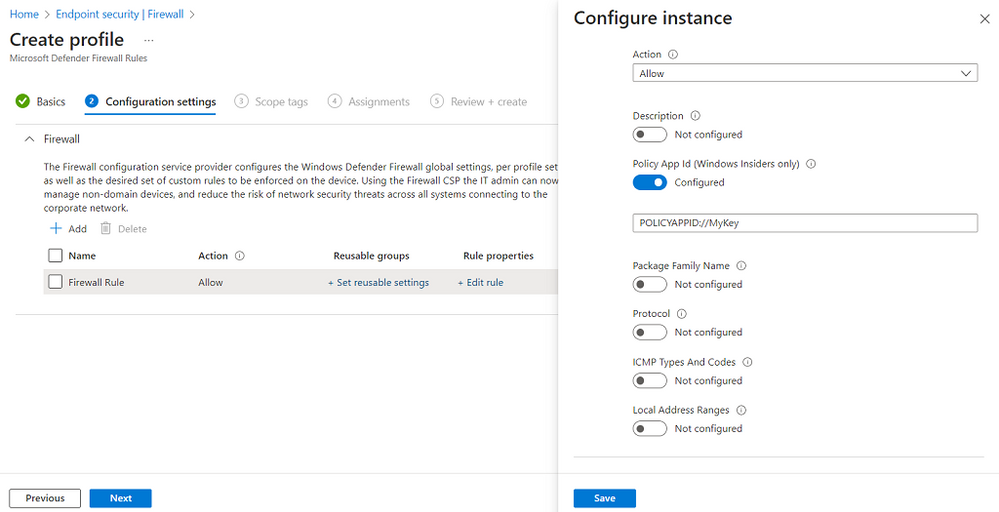
Windows Firewall now supports the use of Windows Defender Application Control (WDAC) Application ID (AppID) tags in firewall rules. With this capability, you'll be able to scope your firewall rules to an application or a group of applications and rely on WDAC policies to define those applications. The WDAC AppID functionality adds an administrator defined tag to the given process token. By using these tags, the Firewall Rules policy won't need to rely on an absolute file path or use of a variable file path that can reduce the rule security.
Use of this capability requires you to have WDAC policies in place, which include AppId tags. When creating firewall rules with Intune Microsoft Defender Firewall Rules, provide the AppId tag in the Policy App ID setting. For guidance on creating an AppID using the WDAC wizard, see WDAC Application ID (AppId) Tagging guide.
Security admins can specify one AppId tag within a given Firewall Rule. The format allows for a string of any alphanumeric characters, including ":", "/", ".", and "_".
Consider the following prerequisites for successful configuration:
- The Service Name setting can’t be configured at same time. If it’s configured, the Firewall Rule will fail as will the subsequent rules, which will report errors.
- Some firewall rules may still apply to the device if they’re processed before the failing rules in the sequence.
- If the Policy AppID is configured in the Intune Firewall Rule, then the rule will only apply to devices that match the criteria established by the rule.
- For Firewall rules targeted to unsupported devices (such as Windows 10 20H2 or earlier), the policy will not be applicable to the device and the previous configuration will stay on the device.
This applies to Windows 11. Support for Windows 10 20H2 and later is coming with windows updates at the end of April.
Endpoint security Firewall policy support for network list manager settings
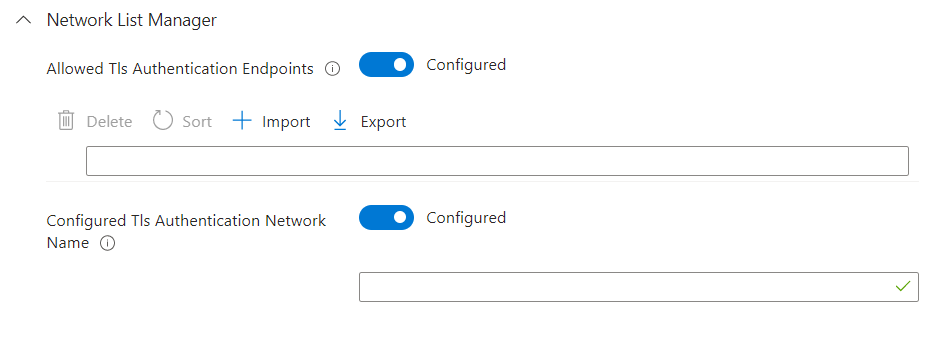
We've added a pair of network list manager settings to the endpoint security Firewall policy. Use the network list manager settings to help determine when an Azure Active Directory (Azure AD) device is on your on-premises domain subnets so that firewall rules can properly apply.
The following settings are found in a new category named Network List Manager, that's available in the Microsoft Defender Firewall profile template for the Windows 10, Windows 11, and Windows Server platform:
- Allowed Tls Authentication Endpoints: This is a list of URLs to endpoints that are accessible only within an enterprise’s network.
- Configured Tls Authentication Network Name: The name of the network authenticated against one of the endpoints listed in the Allowed Tls Authentication Endpoint setting.
For information about Network Categorization settings, see Policy CSP - NetworkListManager.
This applies to Windows 10 and Windows 11.
Endpoint security Firewall Rules support for ICMP type
We’ve added a new setting to the Firewall Rules template “ICMP Types and Codes” which allows you to configure inbound and outbound rules for Internet Control Message Protocol (ICMP) as part of a firewall rule. Security admins can manually enter the list of ICMP types and codes or choose to import and export a supported .csv file for easier management.
To specify all ICMP types and codes, use the “*” character. For specific ICMP types and codes, use the “:” character to separate the type and code. For example, 3:4, 1:*. The “*” character can be used to represent any code. The “*” character cannot be used to specify any type; examples such as “*:4” or “*:*” are invalid. If not specified, the default is All.
Consider the following prerequisites for successful configuration:
- Protocol needs to be set to 1.
- If it’s not, the Firewall rule will report as error and subsequent rules won’t be applied to the device. The previous configuration will stay on the device.
- If the ICMP setting is set to Configured in an Intune Firewall rule, then it will only apply to Windows 11 devices.
- If Windows 10 devices are targeted with the Firewall rule, then the rule will report as “Not applicable” and the entire policy will not apply to the device.
- The previous configuration (last version of the applicable policy or Firewall configuration) will stay on the device.
This applies to Windows 11.

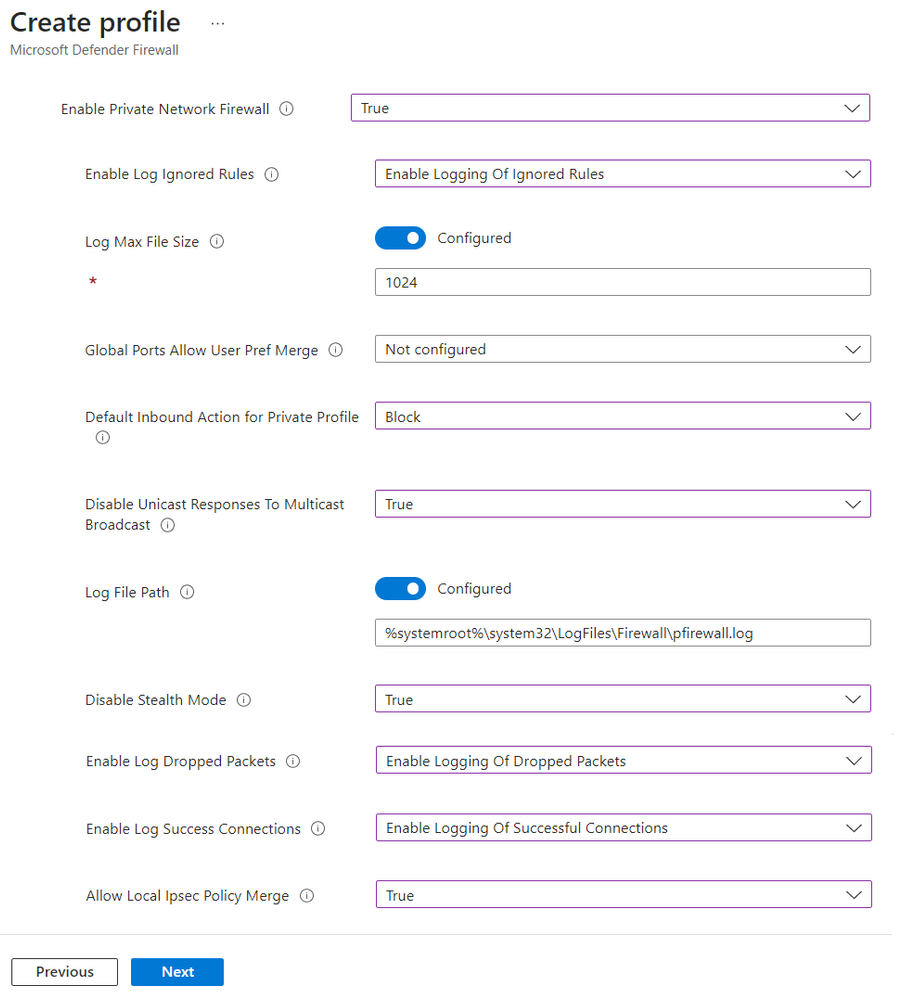
Endpoint security Firewall policy support for log configurations
You can now configure firewall logging options in endpoint security Firewall policy. These settings can be found in the Microsoft Defender Firewall profile template for the Windows 10 and later platform, and are available for the Domain, Private, and Public profiles in that template. The following are the new settings:
- Enable Log Success Connections
- Log File Path
- Enable Log Dropped Packets
- Enable Log Ignored Rules
The settings will apply to Windows 11 devices. If targeted to Windows 10 devices, they will report as “Not applicable.”
Endpoint security firewall rules support for Mobile Broadband (MBB)
The Interface Types setting in endpoint security Firewall policy now includes the option for Mobile Broadband. Interface Types are available in the Microsoft Defender Firewall Rules profile for all platforms that support Windows. For more information about the use of this setting and option, see Firewall CSP.
This applies to Windows 10 and Windows 11.

Note, the previous option has been deprecated and is listed as [Not Supported] Mobile Broadband in the options.
Stay tuned to What’s new for more new features and improvements coming to Microsoft Defender Firewall and Microsoft Intune! If you have any questions, please let us know in the comments or reach out to us on Twitter @IntuneSuppTeam.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.