- Home
- Security, Compliance, and Identity
- Microsoft Defender for Cloud Blog
- Consuming Microsoft Defender for Cloud Data
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Authors: Lara Goldstein, Bar Brownshtein
Introduction
Microsoft Defender for Cloud is a unified solution for cloud security posture management (CSPM), cloud workload protection (CWP), and DevOps security management. Customers using Microsoft Defender for Cloud may want to consume the detailed security alerts, recommendations, secure score controls, and regulatory compliance checks outside of the portal for additional analysis. This blog will walk through different scenarios and methods to retrieve Defender for Cloud data, including exporting to Security Incident Event Management (SIEM) solutions, Log Analytics workspaces, CSV files, and alternative locations via an automated script.
Types of Data Available for Consumption
Before exporting Defender for Cloud data, it is important to understand the type of data available, this will also help you to identity which data you really need to export. The data available from Defender for Cloud that can be exported include:
- Secure score per security control or subscription with details about the assessed resource ID, the control’s display name, the number of healthy and unhealthy resources, the maximum score of the control, and the current score of the control.
- Security recommendations meant to help remediate identified security misconfigurations and weaknesses on resources connected to Defender for Cloud. Data about each recommendation includes the assessed resource ID, recommendation name, description of the recommendation, environment (Azure, AWS, GCP), severity, and state per resource (healthy, unhealthy, not applicable).
- Security findings that belong to a ‘parent’ recommendation. Security findings are also known as nested recommendations. Examples of nested recommendations are the individual vulnerability findings for the parent recommendation ‘Machines should have vulnerability findings resolved’.
- Security alerts generated by different workload protection plans. Each security alert contains information about the alert name, severity, compromised entity, start time, end time, status (active, dismissed, resolved), and relevant MITRE tactics and techniques.
- Regulatory compliance assessment states for different regulatory standards (e.g., PCI DSS 3.2.1, NIST SP 800-53) that have been assigned to subscriptions and multicloud connectors. Data regarding the assessed resource ID, compliance control, compliance standard, number of passed and failed resources, and state of the assessment can be exported.
Scenario 1 - Exporting Data to your SIEM
Defender for Cloud can stream the data listed in the above section to different SIEM solutions, including IBM QRadar, Splunk, and Microsoft Sentinel. This is useful because a SIEM delivers visibility into the full kill chain across the entire organization, including third party data. Data provided by Defender for Cloud regarding a resource’s state, misconfigurations, and attacks, is valuable to have in SIEM solutions, especially since customers tend to use SIEMs as their single pane of glass for incident triage.
There are different methods for streaming Defender for Cloud data to SIEM solution, including continuous export to Azure Event Hub and integration with Microsoft Graph Security API. The following documents describe the process of configuring the integrations:
- Stream your alerts from Microsoft Defender for Cloud to Security Information and Event Management (S....
- Set up the required Azure resources to export security alerts to IBM QRadar and Splunk | Microsoft L....
Scenario 2 - Exporting Data to Log Analytics
Many customers want to analyze Defender for Cloud data inside a Log Analytics workspace to centralize information, view Azure alerts alongside Defender for Cloud alerts, retain Defender for Cloud data through Log Analytics data retention policies, and power some of the built-in workbooks to track secure score and compliance over time.
For customers using Microsoft Sentinel, the best practice is to centralize alerts in Sentinel using the built-in connector. However, if customers want to see recommendations, secure score information, and compliance assessments alongside the alerts in Sentinel for more context, it is recommended that they set up continuous export to Log Analytics.
To set up continuous export to Log Analytics, follow the guidance provided in this document.
When Defender for Cloud data is streamed to a Log Analytics workspace, customers can analyze the information in the following tables:
- Secure Score Controls
- Secure Scores
- Security Recommendations
- Security Nested Recommendations
- Security Alerts
- Security Regulatory Compliance
Scenario 3 - Exporting Data to CSV
There are specific scenarios where customers may want to manually download a list of relevant recommendations, regulatory compliance controls, and security alerts from Defender for Cloud to share with others within their organization. Some examples of these scenarios include:
- Comparing alerts generated by Defender for Cloud against alerts generated by other tools for evaluation purposes.
- Showing leadership the status of unhealthy recommendations in the tenant.
- Sharing a list of all high severity unhealthy recommendations within a subscription or resource group to the owner to triage.
- Downloading a list of all exemptions created within the tenant for audit reviews.
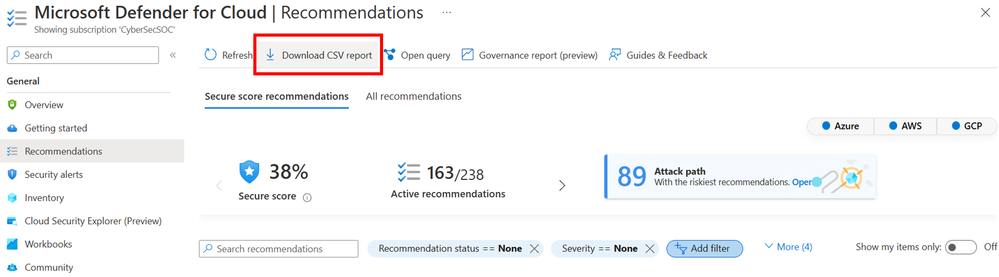
For these one-off scenarios, Defender for Cloud offers the option to export data to CSV. Customers can perform this action directly from the Recommendations, Inventory, Security alerts, and Regulatory compliance blades within Defender for Cloud. After configuring any relevant filters (e.g., only show recommendations for resources in a specific resource group, only show recommendations for a specific resource type), the customer can select “Download CSV report” to export the data out of the portal.
Customers who want more flexibility can also query Azure Resource Graph (ARG) directly for relevant information regarding their Defender for Cloud environment and export the results from ARG.
Scenario 4 - Exporting Data Using Automated Scripts
Automated scripts can simplify the task of exporting Azure security artifacts and make it more efficient.
By using a script, security recommendations can be automatically exported in a timely and consistent manner, providing a comprehensive report on the security posture of Azure/AWS/GCP environments.
Here is an example of how to export High severity Azure recommendations C# code that can be executed in a console application or integrated as part of an existing project:
using Azure.Identity;
using Azure.ResourceManager.ResourceGraph.Models;
using Azure.ResourceManager;
using Azure.ResourceManager.ResourceGraph;
using Azure;
namespace ExportRecommendationsFromArg
{
class Program
{
static async Task Main(string[] args)
{
//---------- CLIENT CONFIGURATION ----------
var tenantId = "<ADD-TENANT-ID>";
// Create new client (if needed) using this guide: https://learn.microsoft.com/en-us/azure/active-directory/develop/howto-create-service-principal-portal
var clientId = "<ADD-CLIENT-ID>";
// Generate Client secret using this guide: https://learn.microsoft.com/en-us/azure/industry/training-services/microsoft-community-training/frequently-asked-questions/generate-new-clientsecret-link-to-key-vault
var clientSecret = "<ADD-CLIENT-SECRET>";
//-----------------------------------
//---------- QUERY CONFIGURATION ----------
// You can modify the below query to retrieve the data you need. The following query retrieves all Azure recommendations with high severity.
// You can also filter data one specific subscriptions if needed (Otherwise it will return data from the tenant).
var query = @"securityresources
| where type == 'microsoft.security/assessments'
| where properties.resourceDetails.Source == 'Azure'
| where properties.metadata.severity == 'High'";
//-----------------------------------
var client = new ArmClient(new ClientSecretCredential(tenantId, clientId, clientSecret));
var tenant = client.GetTenants().First();
long totalOfRecordsRetrieved = 0;
ResourceQueryResult result = null;
var queryContent = new ResourceQueryContent(query)
{
Options = new ResourceQueryRequestOptions()
{
}
};
Console.WriteLine($"Start retrieving records from ARG");
do
{
var response = tenant.GetResources(queryContent);
result = response.Value;
/*
* Proccess the current page of your data here
*/
totalOfRecordsRetrieved += response.Value.Count;
Console.WriteLine($"Number of results retrieved: {totalOfRecordsRetrieved} total of {response.Value.TotalRecords} records");
queryContent.Options.SkipToken = response.Value.SkipToken;
} while (result.SkipToken != null)
Console.WriteLine($"All records retrieved succesfully");
}
}
}
Conclusion
This article described different methods to consume Defender for Cloud recommendations, alerts, secure score information, and compliance checks outside of the portal for data centralization, incident triaging, and communication purposes.
More Information
- What is Microsoft Defender for Cloud? - Microsoft Defender for Cloud | Microsoft Learn
- Continuous export can send Microsoft Defender for Cloud's alerts and recommendations to Log Analytic...
- Continuously Export Microsoft Defender for Cloud Alerts and Recommendations via Policy - Microsoft C...
Reviewers
- Yuri Diogenes, Principal PM Manager
- Or Serok Jeppa, Senior PM Lead
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.