- Home
- Security, Compliance, and Identity
- Microsoft Defender for Office 365 Blog
- Email Protection Basics in Microsoft 365: Anti-malware, Safe Attachments, and Quarantine
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Email Protection Basics in Microsoft 365: Anti-malware, Safe Attachments, and Quarantine
Microsoft Support is excited to continue this blog series that will demystify how Microsoft 365 email protection works. In this fourth part of the series, we will cover how anti-malware and Safe Attachments protections work for known and unknown threats and review common quarantine operations, quarantine policies and notifications.
Anti-malware protection
Email attachments that contain malicious applications or code can cause damage and disrupt normal use of users’ devices. These malware attachments can allow unauthorized access, use system resources, steal passwords, lock users or admins out of their computer, or ask for ransom. Major malware categories are viruses, spyware, and ransomware.
Learn more about malware and ransomware protection in Microsoft 365.
Anti-malware policies
Exchange Online Protection (EOP) provides a multi-layered anti-malware protection that is designed to catch all known malware that travels into or out of your organization on multiple platforms. Anti-malware protection uses real-time threat response during malware outbreaks, and fast deployment of anti-malware definitions which keep the engines up to date. All Microsoft 365 organizations and EOP standalone customers have a built-in anti-malware policy called Default.
Learn more on how to configure anti-malware policies in the Microsoft 365 Defender portal.
Tip: Bookmark this quick link to go straight to anti-malware policies: https://security.microsoft.com/antimalware
With Microsoft Defender for Office 365, you get additional protection against unknown malware risks with Safe Attachments. Read on for details.
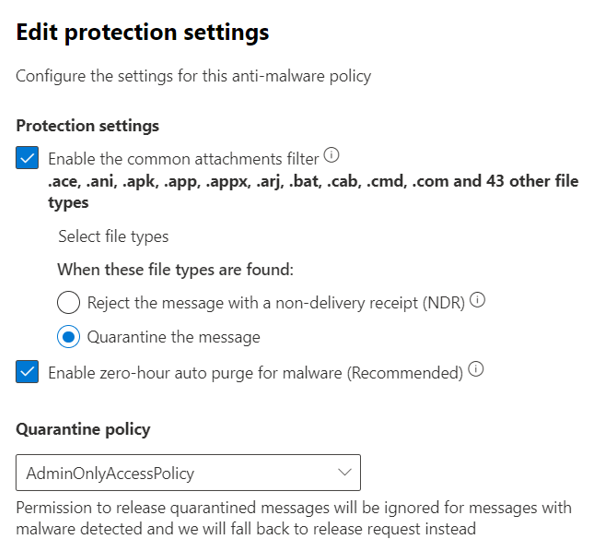
Common Attachment Filter
It is a common practice to share attachments in emails. These attachments could be of any type—documents, pictures, music files, pdfs, plain text files, and at times, proprietary file types, each serving their use to the recipients. However, not all files are good, and sometimes can be shared for malicious intent.
Threat research confirms there are over 50 file types, like executable files (.exe or .com) that no one should send through email. Such files can infect your endpoint devices, and install viruses, trojans, or information stealing programs. Common attachment filter comes with a default selection of these file types to block them out of the box and allow you to customize the file type list. It uses true typing for most common files, so that when someone tries to rename the file to evade the filter, true typing attempts to detect the true file type where supported most of the time and falls back to extension matching. Microsoft highly recommends keeping this filter enabled.
Malware Zero-hour Auto Purge
Threat actors commonly send benign messages and weaponize them later. If the message is detected to contain malware after delivery, Microsoft will “zap” it out of the mailbox and into quarantine with zero-hour auto purge. This setting is also enabled by default, and it is highly recommended that you keep it on.
Learn more and watch a 2-minute video on how ZAP works and how to view post-delivery reports.
Actions and notifications
If the anti-virus engines detect malware in any of the attachments, the message is automatically sent to quarantine, where the administrator can review it, if need be. The recipient will get a notification only if this configured in the quarantine policy.
Same goes for attachments where the file type matches those configured in your common attachment filter policies. However, the administrator can choose one of the two actions on file type detections: reject the message and notify the sender or quarantine the message.
The default is to reject the message with a non-deliverable report (NDR). The sender will receive the following NDR:
“550 5.0.350 One or more of the attachments in your email is of a file type that is NOT allowed by the recipient’s organization”.
No notification would be sent to the recipients or your administrators.
When you opt to quarantine the messages, this will allow your SecOps teams or quarantine administrators to view them, download them for analysis, notify recipients, or release messages to recipients after careful review. Quarantine operations and notifications are covered later in this article.
Figure 1: Anti-malware policy protection settings in Microsoft 365 Defender
Safe Attachments in Microsoft Defender for Office 365 extend the default anti-malware protection set with another layer of protection. Let’s review how Safe Attachments cover the unknown threats.
Safe Attachments
Safe Attachments for Microsoft Defender for Office 365 keep your organization safe from zero-day (unknown) threats by scanning incoming attachments in a special environment to detect malicious intent before they are delivered to recipients. This process is known as sandbox detonation. This gives you another layer of protection tightly integrated with Safe Links in Microsoft Defender for Office 365, and scans multiple layers of attachments (e.g., emails with an attachment, attachment with an attachment, links leading to download an attachment, and so on).
Learn more about Safe Attachments.
A preset security policy called “Built-in protection” keeps all paying Microsoft Defender for Office 365 customers secure with Safe Attachments protection, even if you have never set it up. The Built-in protection automatically covers any new users onboarded. You can create and customize new Safe Attachments policies or apply them for specific sets of recipients.
Figure 2: Safe Attachments policies in Microsoft 365 Defender
Actions and notifications
When the Safe Attachment policies identify any of the attachments as malicious, one of the following actions is taken—Monitor, Block, or Dynamic Delivery. If you choose the Monitor action, messages with detected malware will not be blocked. This will allow you to track scanning results using Microsoft 365 Defender reports. This is useful for testing a policy with a limited recipient scope.
With the Block action, messages detected by Safe Attachments as containing malicious content will be quarantined to prevent recipients from opening or sharing them. You can opt to notify your users about these detections by selecting the appropriate quarantine policy to apply to these messages.
Dynamic Delivery allows your users to receive the email without attachments first, and then the attachments are accessible once the file scanning is complete, and no threats are found.
Dynamic Delivery will not apply to messages where the original message cannot be found to reattach the files after scanning, mainly if it was moved by an inbox rule or deleted. That is why Microsoft highly recommends opting for the Block action in your policies.
Learn more on Safe Attachments on Microsoft Learn or go to the Settings page directly at https://security.microsoft.com/safeattachmentv2.
Figure 3: Safe Attachments unknown malware response settings in Microsoft 365 Defender
Tip: Although this blog series is focused on email protection, do not forget to review and configure Safe Attachments for SharePoint, OneDrive, and Microsoft Teams, as well.
Managing false positive and false negatives
Users sometimes report legitimate attachments incorrectly classified as malware (false positives). What are your options if, for example, an application you control and know is safe sends an important email attachment to internal users, and your policy quarantines it as malware? Or what should you do when a malicious message reaches your users’ inbox, and you believe it should have been identified as malware and blocked by the filters (false negative)?
Legitimate attachments blocked as malware
Start by reporting false positives to Microsoft on the Submissions page in Microsoft 365 Defender. Check the page after a while to learn what happened, and if the original verdict has changed. Send the message again later to confirm. Microsoft Defender for Office 365 Plan 2 customers can also adjust alerts or undo remediation actions, in addition to reporting the message. Learn how to report false positives or false negatives following automated investigation in Microsoft Defender fo...
Go directly to Submissions at https://security.microsoft.com/reportsubmission.
Figure 4: Submit messages to Microsoft for analysis in Microsoft 365 Defender
Usually, files are blocked due to anti-malware policy settings. In that case, the Result column will advise you to update or remove the file types from the common attachment filter and ask you to specify the exact policy being used.
For example, here’s the Result column outputs for a policy named “Default”:
Blocked due to a policy. Update or remove the "FileTypePolicy" action from the Anti-malware policy (Default) so that the system's recommended action can be taken.
When you select the submission details, the details pane on the right will include the reason for blocking the message and information about all the attachments that were included in the message:
Blocked by organization policy: Antimalware policy block by file type
Figure 5: Submission details pane, including attachments
You will see CAT:FTBP in the message headers in quarantine, when the common attachment filter has blocked the message as malware.
CIP:255.255.255.255;CTRY:;LANG:en;SCL:9;SRV:;IPV:NLI;SFV:SKI;H:PR3PR07MB8157.eurprd07.prod.outlook.com;PTR:;CAT:FTBP;SFS:;DIR:INB;
Once you deselect the blocked file type and resend the message, it should then go through successfully.
Tip: Non-delivery reports (NDRs), quarantine, or message traces can also help identify why messages are blocked. You can also use Threat protection status report, where you can view malware-blocked messages, among other useful email protection views. When tracing messages in Exchange Admin Center, choose the extended message report to download a .csv file with the results. The Custom Data field contains detailed information about the detection.
Here is a sample Custom Data field output, which shows an email quarantined as malware (Type=Malware), the relevant quarantine policy tag (AdminOnlyAccessPolicy), how often users are notified part of this quarantine policy (here: never, since this is an Admin only quarantine policy - EsnFrequency=0), and the anti-malware policy name that quarantined it (Default:(
S:CFA=LTC|RPLHCFR=3|RPLSLR=1|RPLAPR=0|RPLMR=4|RPL=8|RSP=0;S:QIA=SUM|Type=Malware|Expire=2022-12-25|PartName=qblob-8394-286|MimeName=8dbc72d4-1434-4b90-7583-08dacfxxxxx|EsnFrequency=0|QuarantineTagName=AdminOnlyAccessPolicy|RuleName=Default|PolicyId=2071c751-43e0-452f-a602-97e9f23xxxxx|PolicyType=AntiMalwarePolicy;S:CompCost=C|ETR=1;S:DeliveryPriority=Low;S:PrioritizationReason=AS-Message-Spam;S:AccountForest=FFO.extest.microsoft.com
True-type detection is when a file type that is in your common attachment filtering list triggers a detection even if the file type in the message is different. Common examples are .wmf pictures filtered as .wmz file types (.wmz are compressed versions of .wmf files). So, if your organization needs to receive .wmz file types, remove .wmf from the common attachment filter in your anti-malware policies.
Just like the other email protection policies in Microsoft 365 Defender, anti-malware policies are recipient-based. That means that you can apply separate policies for different users, groups, or domains. Try not to create overlapping policy scopes, but if you do, the higher-priority policy wins. Lower priority values mean higher priority order, so a policy with priority “0” is executed before the policy with priority “2”. Learn more on order and precedence of policies in the previous part of this series.
True-type detection example:
Erica is an administrative assistant in Contoso. She has created a new email signature that includes an image. Shortly after, Erica’s recipients have noticed they stopped receiving her messages. She contacts the IT administrator for assistance.
Figure 6: Email signature containing an embedded image
Although images are embedded inside the message body, they are scanned as files by the anti-malware policies. The administrator traces Erica’s messages and finds that all her outgoing emails are in quarantine with the true type .wmf detected in the message. When analyzing the HTML source of the message, the embedded .wmz file is observed:
<v:imagedata src="cid:image002.wmz@01D8FE5F.3DBB4160" o:title="" />
<w:wrap type="square"/>
</v:shape>
To resolve the issue, the administrator may perform the following tasks:
1) Define a temporary new anti-malware policy where only Erica’s department is allowed to send and receive .wmf files by removing .wmf from the list of blocked attachment file types in the common attachment filter.
2) Work with Erica to ensure future signatures are sent in a non-blocked format moving forward.
If your organization requires common attachment filtering exclusions per sender, use the mail flow (transport) rules in Exchange Admin Center. Scope your rules carefully, as setting up any permanent or overly broad overrides is not recommended.
For more information, see Use mail flow rules to inspect message attachments in Exchange Online and Common attachment blocking scenarios for mail flow rules in Exchange Online.
Missed malware
Report missed malware to Microsoft on the Submissions page in Microsoft 365 Defender. Choose Block this file if you want messages with this file to be blocked as malware.
Review Submit malware and non-malware to Microsoft for analysis for additional information on file submissions via this and other methods.
Tip: To block files throughout your organization using their SHA256 hash values, use the Tenant Allow/Block List. This is particularly useful when reporting multiple file hashes, up to 20 at a time.
For how to triage and release messages and set up quarantine notifications for your users, see the next section on quarantine operations.
Quarantine operations
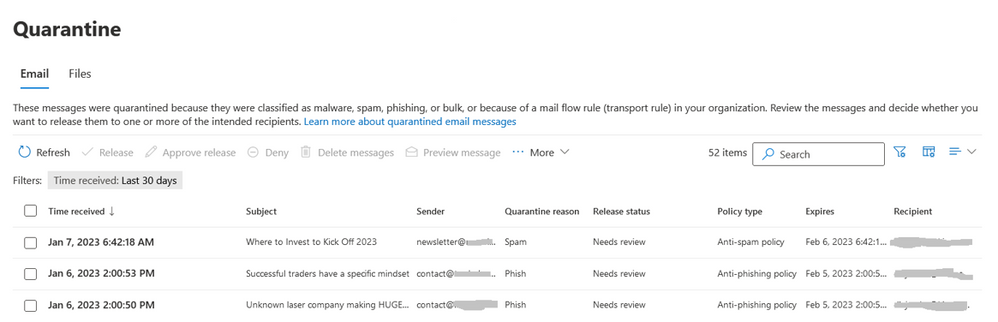
Quarantine in Microsoft 365 Defender is accessible both to administrators and users and has undergone many recent enhancements. For example, the default view now allows you to quickly triage messages and files, find the reason they were quarantined (e.g., spam, phish, malware, or mail flow rules), whether they were released already, or need your review. You can customize columns and add fields, such as Recipient, Message ID, Policy name, Message size, Mail direction and more, which will make your triage even more efficient.
Significant differences between user and administrator quarantine operations
- Your users will not be able to release items with malware on their own from email notifications. They will be able to request the administrator to release it for them from an email notification.
- The tenant administrator always has access to all items in quarantine, including malware. By default, users cannot access or view any high-risk items in their Quarantine view in Microsoft 365 Defender portal.
The following table highlights the main differences. Note that high confidence phish and malware are high risk items.
Table 1: The differences between administrator and user quarantine operations
* Users can release items from quarantine notifications when the administrators configure the appropriate quarantine policies. Administrators may also opt to set up quarantine policies for users to be able to request release of high risk items by applying appropriate quarantine policies to the anti-phishing and anti-malware threat policies. See the next section on quarantine policies for details.
View, release, and download messages from quarantine
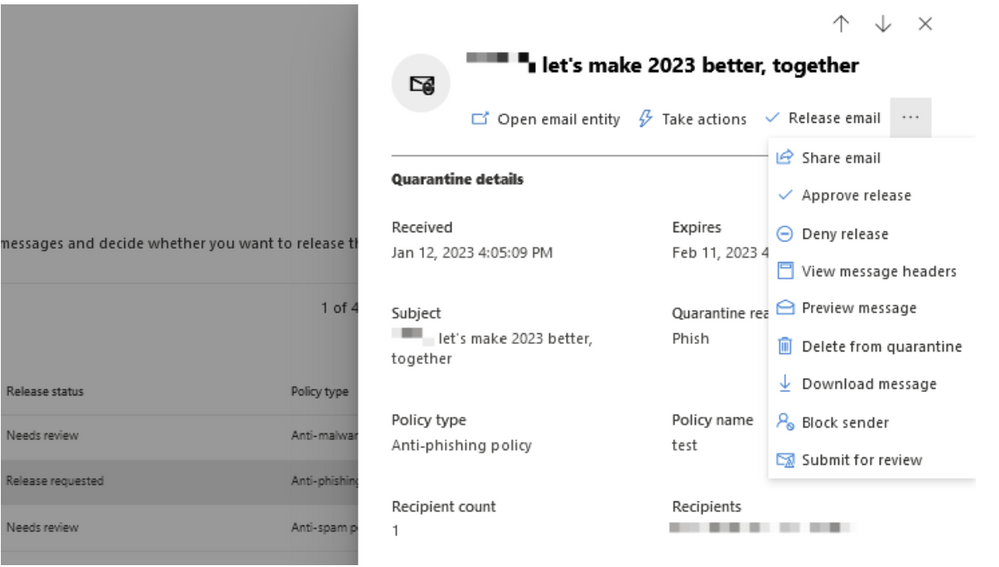
Start your triage by selecting a quarantined message:
Figure 7: Quarantine in Microsoft 365 Defender
This opens the details pane on the right-hand side of the screen, which includes information about threats, attachments, or URLs found in the message, the policy that quarantined the message, email authentication verdicts, and more. Microsoft Defender for Office 365 customers can also pivot from this pane to the email entity page, or take actions, such as launching automated investigations.
Figure 8: Quarantine message details pane in Microsoft 365 Defender
You can select some or all recipients or add new ones to release messages. You can also submit a false positive to Microsoft for analysis to improve detections, if applicable, right from this menu. Track the submission results later on the Microsoft 365 Defender Submissions page.
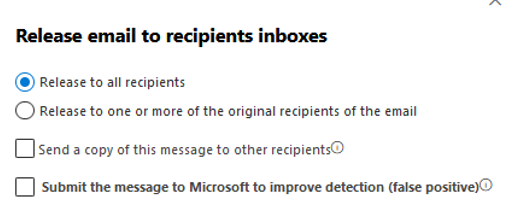
Figure 9: Release email to recipient's inboxes options in Microsoft 365 Defender,
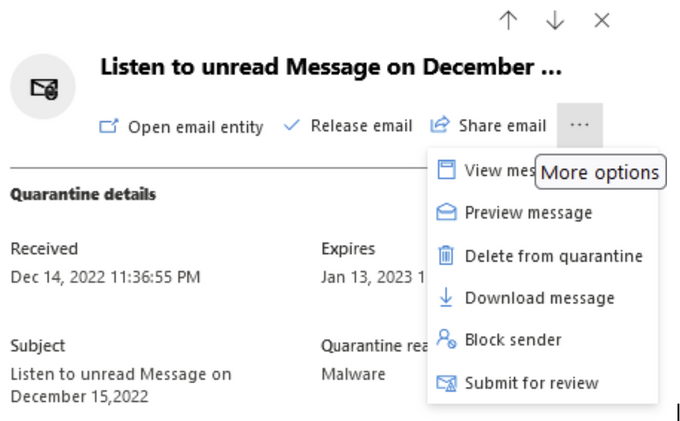
SecOps teams in some organizations may need to download malware samples for additional analysis. Select Download message to safely download the item in a password-protected compressed file.
Figure 10: Download message option in Microsoft 365 Defender
The default retention period for messages is either 15 days or 30 days, depending on the policy, and you can customize expirations in threat policies. For details, visit Quarantined email messages.
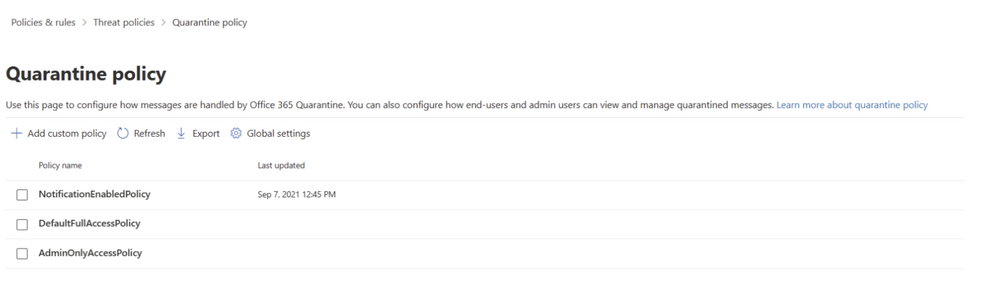
Quarantine policies
Administrators control whether to allow users to release spam, bulk, or suspected phish messages from quarantine. Once you set up policies to request message release, make sure to also configure alert policies to deliver these requests to the appropriate administrators. Otherwise, they will be sent to all administrators who are members of your Organization Management role group.
Follow our step-by-step guide on Quarantine Policies for help or view the full Quarantine Policies documentation on Microsoft Learn.
Figure 11: Quarantine policy in Microsoft 365 Defender
Once quarantine policies are created, apply them to any of your existing threat policies, such as anti-malware or Safe Attachments. See Figure 1 and Figure 3 in this article as examples.
Quarantine Notifications
You can choose to notify your users as frequently as every day or once in 15 days. Most customers opt for daily notifications. Due to this popular customer demand, this frequency will soon include the options to send notifications every four hours, daily or weekly.
Tip: If your users want to access and review their quarantined items more frequently, they can always open https://security.microsoft.com/quarantine at any time.
Quarantine notifications settings, message customizations, logos, and send intervals are set at the organization level, at https://security.microsoft.com/quarantinePolicies.
This is where you can upload a custom logo, set the language for notifications, and change the default sender address from quarantine@messaging.microsoft.com to an address your users will be more comfortable seeing.
Quarantine notification example:
Here is an example of the notification for a phish message. Note that the Release message button is missing. This is because the administrator set a quarantine policy, where the end-user is limited in their allowed actions, and must select Request Release, if they want to get it in their inbox.
Figure 12: Sample email of end-user quarantine notification in English
Once the user selects the Request release option in the email, the administrators will be notified, and will be asked to release or deny the request:
Figure 13: Administrator's Approve/Deny options
Learn more about requesting release in this 4-minute video: Manage the admin quarantine in Microsoft Defender for Office 365.
Quarantine notification language
The language of the notification depends on the regional configuration of each mailbox. To verify regional configuration for Exchange Online mailboxes, run this Exchange Online PowerShell cmdlet:
Get-MailboxRegionalConfiguration john.doe@contoso.com | fl Language
For mailboxes hosted on-premises, the notification language will follow the global settings as shown above. To confirm the language, run this cmdlet:
Get-HostedContentFilterPolicy Default | fl EndUserSpamNotificationLanguage
The value Default means English here unless you had changed the language previously in the global settings.
We hope this article helped you understand anti-malware, Safe Attachments, and quarantine operations better.
Do you have questions or feedback about Microsoft Defender for Office 365? Engage with the community and Microsoft experts in the Defender for Office 365 forum.
Click here to view additional posts in this series. Would you like us to cover more topics? Let us know in the comments.
Important resources:
Malware and ransomware protection in Microsoft 365
Submit malware and non-malware to Microsoft for analysis
Recommended settings for EOP and Microsoft Defender for Office 365 security
Connect to Exchange Online PowerShell
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.