- Home
- Security, Compliance, and Identity
- Microsoft Defender Threat Intelligence Blog
- What's New: Intel Profiles Deliver Crucial Information, Context About Threats
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
We're thrilled to introduce Intel Profiles, a single, reliable source of information in Microsoft Defender Threat Intelligence (Defender TI) security operations teams can use to have instant insight into the threat ecosystem, including pertinent details about vulnerabilities, threat actors, and infrastructure used in attacks. Intel profiles combine 65 trillion threat signals with the expertise of over 8,500 dedicated security professionals to translate that global threat landscape into immediately actionable insights. By comprehending their tactics, infrastructure, and methods of operation, security teams can take proactive steps to prevent threat actors from breaching their organization's defenses.
Users can access Intel Profiles in the Defender TI Portal or the Microsoft 365 Defender Portal.
Accessing Intel Profiles the Defender TI Portal:
Defender TI is now available to licensed customers directly within the Microsoft 365 Defender portal to deliver powerful intelligence that helps analysts correlate information and provides immediate context about threats during their investigations, all within a single unified experience.
Accessing Intel Profiles within the M365D Portal (Click the tab in the menu on the left side):
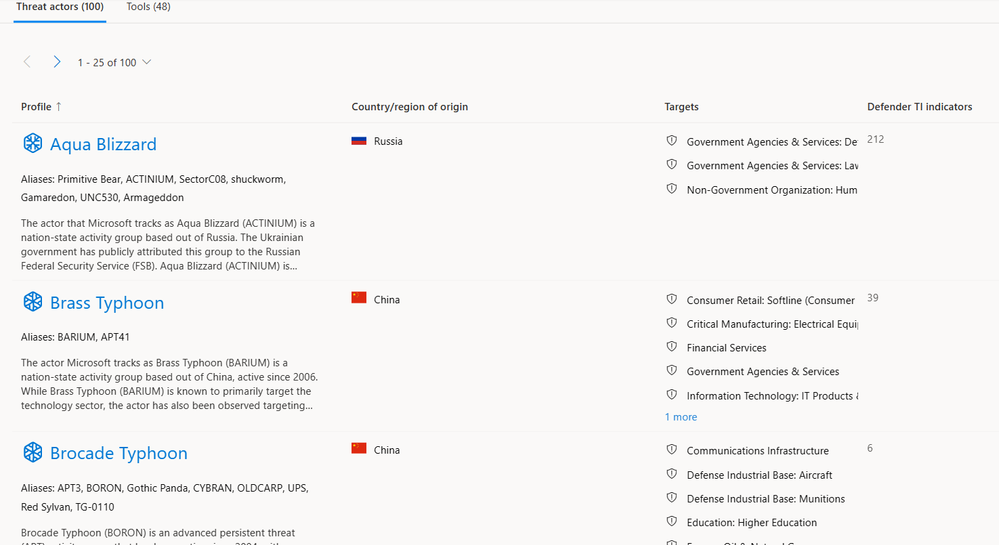
Intel Profiles in Defender TI categorize threat actors based on location, specific target industries, and modus operandi. These profiles include all known indicators of compromise (IoCs) related to their infrastructure and the tactics, techniques, and procedures (TTPs) they use, updated daily. Defender TI also tracks known tools used in attacks, such as CobaltStrike. If an organization can identify the source of the malicious infrastructure, including domains and IP addresses, it can proactively prevent interaction between its resources and the threat.
Intel Profiles are segmented into two specialties: Threat actors and Tools. These categories provide organizations with a comprehensive understanding of threat actors on the internet, including their targets, attack methods, infrastructure, tooling, and backdoors. Unlike static lists or feeds produced by other Threat Intel firms, Intel Profiles are continually updated with the latest threat intelligence to ensure that organizations have the most current and accurate information to inform their security decisions.
With Defender TI, organizations can identify adversary-threat infrastructure at any scale, from a single threat actor to thousands, enabling them to respond quickly and effectively to potential threats. Intel within Defender TI contains detailed information about threat actor groups, including their aliases, targets, CVEs they typically exploit, the state sponsoring them (if applicable), their TTPs, and IoCs.
Threat actor tools are software or scripts utilized to exploit vulnerabilities or techniques to execute an attack. Threat actors themselves create some tools, while others are commercially available software that anyone can purchase. Red teams often use these commercial tools For penetration testing. They are proficient at keeping libraries of exploits up-to-date and providing an easy way to execute them on targets.
Threat actors incorporate these tools into their attack campaigns by circumventing licensing protections, enabling them to use well-maintained libraries of exploits freely. This tactic also allows them to conceal their activities by avoiding using unique custom software that could be linked to their threat group.
Tool Intel Profiles within Defender TI contain detailed information about the tools used by threat actors, including their purpose, target audience, the threat actors who use them, and indicators where the tool has been found on the internet. This information helps security teams understand the tools utilized by threat actors, anticipate their behavior, and take appropriate actions to protect their organization.
In summary, there are a variety of scenarios where SOC analysts, Threat Hunters, and other Information Security Professionals would need detailed information on Threat Actors and the tools they use to attack individuals, businesses, and governments daily. Threat Actor Intel Profiles will allow those InfoSec Professionals to leverage Defender TI to improve their operations and processes.
Questions?
We hope you found this blog helpful in understanding the value Defender can provide. If you have inquiries regarding threat intelligence use cases mentioned or not mentioned in this blog and are not currently working with a Defender TI Technical Specialist or Global Black Belt, please comment below or email mdti-pm@microsoft.com.
Feedback?
We would love to hear your ideas to improve our Defender TI platform or where our threat intelligence could be used elsewhere across the Microsoft Security ecosystem or other security third-party applications. Feel free to comment below or email mdti-pm@microsoft.com to share that feedback as well. If you are currently working with a Defender TI Technical Specialist or Global Black Belt through this PoC, please communicate your requested use cases and product feedback to them directly.
Learn About New Defender TI Features
Please join our Cloud Security Private Community if you're not a member and follow our Defender TI Private & Public Preview events in our MS Defender TI channel. You will not have access to this Teams channel until you are a Cloud Security Private Community member. Users that would like to help influence the direction/strategy of our Defender TI product are encouraged to sign-up for our Private Preview events. Those participating will earn credit for respective Microsoft product badges delivered by Credly.
Work With Our Sales Team
If you want to work with Defender TI Technical Specialist or Global Black Belt, please contact our Sales team by filling out this form.
Additional Resources
What is Microsoft Defender Threat Intelligence (Defender TI)? | Microsoft Learn
Microsoft Defender Threat Intelligence Blog - Microsoft Community Hub
Become a Microsoft Defender Threat Intelligence Ninja: The complete level 400 training
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.