Video Transcript:
- Coming up, with the velocity and sophistication of cyber-attacks on the rise, we look at significant updates to Microsoft Defender Threat Intelligence, for more detailed and current intel on trending attacks. We’re going to show you how this gives you exclusive access to the same raw attack signals that Microsoft researchers have, enabling you to enrich your investigations and contain threats before they even impact your organization; as well as threat profiles that link threats and their methods to known threat actors, so you can more quickly and easily gauge the severity of the threat, and seek timely specialist assistance if needed. And to walk us through everything, I’m joined today by a Threat Intelligence expert and Microsoft security CVP, Lou Manousos. Welcome!
- Thanks so much, I’m excited to be here!
- Thanks for joining us today. As the expert in Threat Intelligence and also the co-founder of RiskIQ, I know that you’re really well-versed in terms of the mechanics of Threat Intelligence As a discipline, it’s one of the largest areas of security investment we have at Microsoft. We collect over 65 trillion security signals across our services and have around 8,500 cross-discipline security analysts globally building finished intelligence that feeds directly into our XDR and SIEM solutions with Microsoft Defender and Microsoft Sentinel that really triggers threat detection response for your organization. And now with the latest round of updates, even before those reports are published, you’ll be able to see the raw data that our analysts are tracking on active attacks as they unfold, so what’s behind all this?
- Well, as one of the largest cloud security providers, we’re always defending our own services against attack. And so because of that, we know how hard it is to stay current and ahead of active threats. Attackers have new levels of automation to evolve techniques faster than we’ve seen in the past. So for example, if you detect and block a domain, they’ve successfully used in a phishing attack, by the time you’ve done that, they may have modified their methods. They can spin up hundreds of new domains to stay ahead of your detection making it harder for you to keep them out. The only way to turn the tables on them is to be able to track and understand the attack as it evolves. And this is important as they may be targeting your specific organization. By giving you the same and timely raw signal that Microsoft systems and security researchers are analyzing and categorizing, you can build an early warning system into how the attackers are modifying their techniques. So now as the attacker scans and searches your infrastructure, you have a window into their reconnaissance efforts and you could use the raw signal to connect the dots on how they’re evolving attack infrastructure during setup and weaponization. As an example, to carry out a ransomware attack, an attacker might set up domains that look like your domain and pull components from your websites, like images and icons to spoof it, so these newly spun up domains can be linked with what we call host pairs and you can now block them before this attack reaches your doorstep and prevent it before it takes hold again.
- And this really changes the game ’cause normally there has to be a victim first before you can start investigating an attack, so it removes that delta then and what you can defend against because if we take that ransomware example that you just gave, you can see that the attacker is doing stuff outside of your own network and they’re actually planning to evolve their attack. Not only can you get more complete picture then of the entire attack chain across different phases of the attack, but you can also move faster to block and disrupt those attacks before they disrupt you. So, what’s making all this level of visibility possible?
- We now have native integration of RiskIQ data with Microsoft Defender. And this means we can combine the trillions of signals that you mentioned Microsoft tracks across all of our services and endpoints with the breadth of real-time operational information that we’re continually and historically observing across the entire internet. So, this is powerful because we’re crawling the entire internet for these signals and as an attacker interacts with the internet to launch their attacks and campaigns, they’re leaving behind clues as to who they are and we use these clues and signals to forensically trace them as they tactically stage and execute attacks. For example, take a previously unknown attack with a weaponized email that contains malware. First, the email itself contains a lot of metadata and clues so we have the sender’s domain name and links within the email message and more, so we’re able to see the malware in the email, once detonated is calling out to a command-and-control server with an IP address, and this IP address in turn has an SSL certificate on it. This cert is associated with additional IP addresses and some of those point to domains, so now even though those domains are different, we now know they’re part of the same attack and additional layers of information on the web might be contained from cookies and certs and even emails in domain registrations, it all links this attack together. So, there may be a whole new piece of malware that we didn’t know about related to this same attack, so you’re able to map the actions within the signal of the attacker. So the raw data we give you in Threat Intelligence lets you look at internet signals to chain together a 360 degree view on the evolving attack infrastructure. And this enables you to investigate users or apps and even devices that may be communicating with it and vice versa, so this is living intelligence. We’ll link in threat patterns and methods to known threat actors who we assign threat profiles. So our cross-discipline teams, we’ve been tracking hundreds of threat actors for decades. This includes nation state threat actors and cyber criminals using ransomware and more, so the depth and breadth of actionable signal that we give you that can be scoped in the context of your organization, this is going to take your rapid investigation and incident response to the next level. It’s totally unparalleled and unique.
- So, how quick though is that raw intelligence then on the attack available? And can you show us what it looks like to use it?
- Sure. Because we’re collecting this data and directly through our own systems, you get access to the intelligence faster than anywhere else and we don’t just add a few known indicators and then just move on to the next one. These are live queries and data associations that we’re constantly adding to. You can dig into the raw data from our new Threat Intelligence experience. This is built right into Microsoft 365 Defender. There’s also a standalone portal which I’ll show you in a sec. So in the middle of the screen, this is where you can search against dynamic Threat Intelligence. From here, you can target your search on specific types of results, anything from the threat actor’s name, to IP addresses, script names, and more. So, it’ll then search over exclusive Microsoft Threat Intelligence, this is the stuff that’s not even published anywhere else. Plus, we also have Open-Source Intelligence or OSINT articles. This way, you’ve got everything in one place. On the left side, this is where you get to our new Threat Intel Profiles. Intel Profiles, as mentioned, give you critical updated information, including the indicators of compromise on the threat actor groups and the malicious tools that those threat actors are leveraging.
- So, how would I use this then to kind of translate it for my industry or my organization?
- So, one good way is to start with what you already know and to search for it. For example, if a specific threat actor is operating in your industry, you can look them up and proactively block aspects of their attack infrastructure. In this case, I’ve heard about a new threat using a component called Manage Engine, so I’ve searched for it and you’ll see the top result indicates activity from a threat actor we’ve named Phosphorus. So, I’ll dig into the activity snapshot. And here, I see information about a vulnerability. So, let’s look up their Intel Profile. It shows us that it’s an Iranian group and from there, I get a better understanding of what their capabilities are and who they’re targeting, along with all the active CVEs that they utilize. The CVE card shows us that it’s actually a remote code execution and how that works. In related articles, you’ll see additional reporting from Microsoft and OSINT for this vulnerability. And by searching for Phosphorus directly, I can stay up to date with any new intel discovered from Phosphorus as this group continues to develop.
- And this is where knowing if that threat actor then is well-known and well-resourced, you know, it’s maybe a potential nation state, like you mentioned, it’s going to help you kind of assess the level of risk and just how bad it is.
- That’s right, and this gives you an opportunity to actually plan your response. While you might handle incidents from a smaller threat actor internally, if you find nation state threat actors targeting your organization, this is where you’re going to proactively pull in investigators from the government or law enforcement to help.
- So, how do you connect then this threat actor then to an active incident that you might be triaging with your SecOps team?
- Sure. Let me show you how that works in the context of an active attack. And by the way, everything I’m showing you is real intelligence based on real threat actors that we are tracking. In this example, we start in your SIEM. We support all SIEMs, but in this case, I’ll show you this in Microsoft Sentinel. Here, we’ve detected a malicious IP downloaded some SAP data. And we can look at the external IP address in this attack to get additional intelligence. The threat actor and their tooling HAFNIUM and Cobalt Strike is listed, so let’s dig into those details. This takes me over to the Threat Intelligence console and I can see the same details that we saw in Sentinel, but now I can dig deeper. HAFNIUM, which is the name that Microsoft has assigned to this particular threat actor, has been seen to target a number of industries, including healthcare and defense to name a few, so this is a pretty serious adversary. In the past, the group have exploited zero-day vulnerabilities in Microsoft Exchange, which you’ll see with these CVEs. If I click into their TTPs, or Tactics, Techniques, and Procedures, we’ll see all the methods used during the attack in a lot more detail, as well as the malware that was used by the them. In some cases, they’re using commodity malware that’s not exclusive to them but also used by other threat actors. Then, indicators are all the hashes, domains and IP addresses that have been linked to this threat actor on the internet. So that’s our threat actor, but often equally important is the tooling that they’re using to carry out their attacks. This IP address, as you’ll recall, was associated with the Cobalt Strike tools, which is a pretty common tool in the security community. Within the tool profiles itself, we get this nice list of indicators with known IPs, domains and certs that you can use as part of your investigation.
- Of course, you know, for things like tooling, of course you can put in policies for your managed machines that are going to block those tools regardless of who’s running them, whether that’s internal or external. Why don’t we switch gears though, because yeah, hopefully, we can scale back that attack severity a little bit here. So why don’t you walk us through then how you might use the raw data that you’re getting from Threat Intelligence to actively work through and investigate a running attack?
- Yeah, sounds good. This is an important capability to leverage for Threat Intelligence or investigations. So let me show you how they help you in the case of a rapidly evolving incident. So I’m back here in Sentinel, and we can see a detection made inside of Sentinel using finished intelligence. Someone in the organization tried to access a known bad watchlist domain. And this links me to a published article associated with the domain. The article was first published by sucuri.net, so this was OSINT collected on the internet. It’s a creative phishing campaign using Instagram and Twitter verification to lure users into submitting personal info and steal credentials so what the user is looking for here is that coveted verified social media badge. Here we can see the one original public indicator was published in the article, the domain instagramforbusiness.info. Just to show you what a victim would have seen, the attacker masquerades as Instagram to phish information, and this looks legitimate even to someone who’s seen a lot of phishing campaigns, The images are pulled straight from Instagram, the fonts match, there’s no typos, and even the Instagram street address is correct. 1 Hacker Way. So, you know, a lot of people are striving to have verified account status and it’s really easy to fall for this.
- And one thing I’ve noticed, you know, with these, they get more and more believable and legit every single time they send out a new phishing campaign. I probably would’ve fallen for something like this even myself because there were none of the telltale signs to show it was fake.
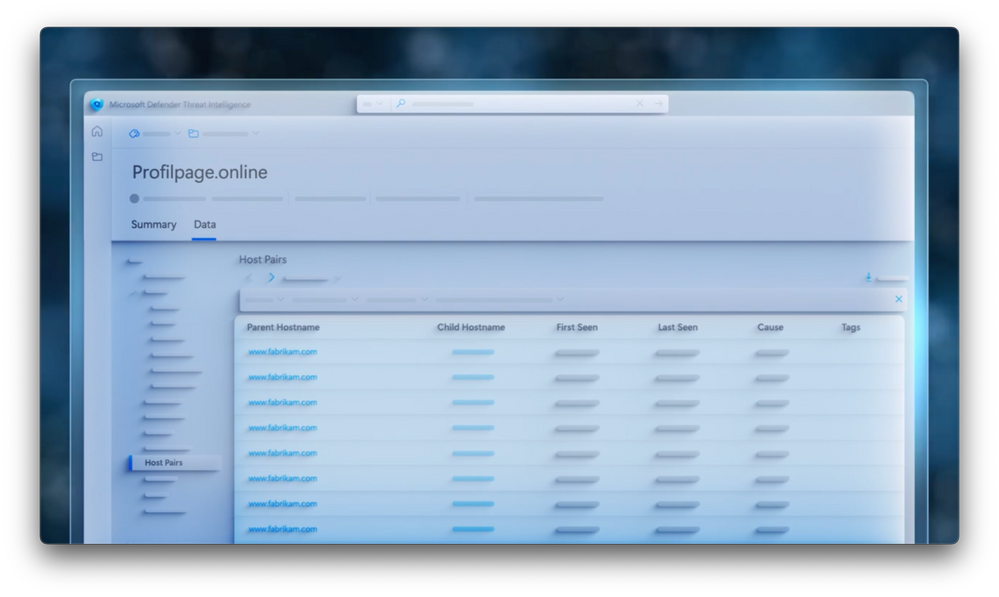
- And you wouldn’t be alone there because often, the attacker are targeting users that have administrative privileges. The method in use here is what we call host pairs, which as I mentioned before, it creates believable phishing sites where they might use legitimate assets from your public domain to spoof it and they often typo-squat your domain as well. So let me show you how you could use Threat Intelligence with host pairs to investigate. Here we can see Microsoft researchers and investigators reviewed this open source article and determined at the time of publication, there were 250 additional indicators. But that was about six months ago, so it’s evolved since then. The domain at the bottom that looks like confirmed Instagram is a domain where we have seen traffic. And so to get a more current view, we can drill into the data and see the most up-to-date host pairs associated with it. One thing you’ll see when researching this particular case is that both the original indicator domain from security, instagramforbusiness.info and the domain Adele hit on in our environment both have newbigdata.science. And we can see that this domain has been around since 2018. So let’s take a look at its host pairs. And we can see that there’s over 3,000 domains that are listed, and some appear to be running a script and others have iframe. So let’s just filter it down in the list that are running scripts. That gets us down to about 1,500 domains, that’s 1,200 more than were originally published with scripts. And now we can take proactive action and investigate whether anyone or any machine in our org has tried to access any of these sites.
- So effectively what you’ve done here is you’ve kind of created your own research, your own dataset that you can pull together that’s going to apply directly to your incident.
- Yeah, now we need to take this information and bring it back to our SIEM. And we can look to see if anyone has interacted with these or other malicious domains. In fact, here we see another machine and user has actually interacted with this domain and we can take the right actions to prevent it from spreading. And from here on, we can keep monitoring Threat Intelligence and watching for new domains, IPs and other indicators to keep them out.
- And all these new updates for Intel Profiles and the raw intelligence that we just saw, it’s available right now, so for anyone who’s watching who’s looking to get started, what do you recommend?
- Get started with threat intel or if you have a threat intel program, expand it to use Microsoft Threat Intelligence. You need every tool in your arsenal to stay ahead of adversaries because their attacks, they’re just going to keep evolving and you need the latest information and an intel-led approach to security. Use Threat Intelligence to better understand the threat landscape, how adversaries operate, and target you or your industry. Enable Threat Intelligence within Microsoft Sentinel and Microsoft 365 Defender today to stay ahead of evolving attacks. And you can learn more at aka.ms/mdti-tech. And if you’re wanting to try Microsoft Thread Intelligence directly, you can also access the most current two weeks of data for free at ti.defender.microsoft.com.
- Great stuff. Thanks so much for joining us today, Lou, and of course, keep checking back to Microsoft Mechanics for all latest tech updates, subscribe to our channel if you haven’t already, and we’ll see you soon.