- Home
- Security, Compliance, and Identity
- Microsoft Sentinel Blog
- Detect capture-replay vulnerabilities & exploits with the Sentinel solution for SAP® applications
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Detect capture-replay vulnerabilities and exploits with Microsoft Sentinel solution for SAP® applications
The Capture Replay Weakness
As per MITRE, authentication bypass by capture-replay is a weakness that exists “when the design of the software makes it possible for a malicious user to sniff network traffic and bypass authentication by replaying it to the server in question to the same effect as the original message (or with minor changes)”. These types of attacks are best prevented by encrypting communications, to avoid exposing authentication tokens and other reusable commands.
Capture-replay Weakness in SAP RFC
With CVE-2023-0014, we learn of a weakness in the remote function call (RFC) framework of SAP, where the system identification is not uniquely determined, allowing an attacker to capture the authentication from normal communication between trusting SAP systems, and reuse it. The SAP correction for this vulnerability (as detailed in the SAP wiki Note 3089413) requires patching of the SAP kernel, the SAP_BASIS component and migration of the existing connections. Once patching is done and migration is complete, a parameter is set at the system level to make sure that only secured trusting connections are allowed.
How the Microsoft Sentinel solution for SAP® applications can help
The Microsoft Sentinel solution for SAP® applications is an add on that allows to extend the state-of-the-art SIEM and SOAR capabilities of Microsoft Sentinel to the security coverage of SAP systems. Shortly after the introduction of this vulnerability, we have added two detections to the solution's content, designed to help identify which systems are vulnerable, and safeguard the RFC trusting mechanism against future tempering.
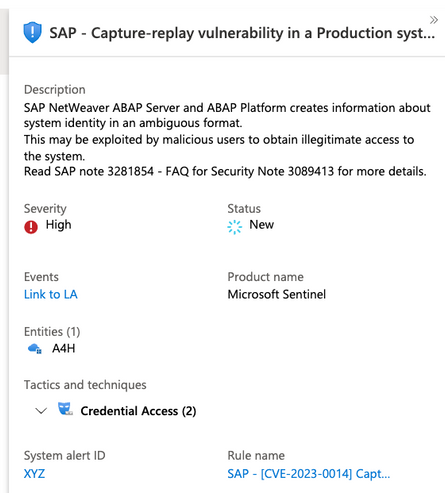
SAP - (Preview) Capture-replay vulnerability in SAP NetWeaver [CVE-2023-0014]
This analytics alert rule investigates your landscape's configuration ingested from SAP table PAHI and specifically the value of parameter 'rfc/allowoldticket4tt' which reflects the status of the fix of this vulnerability. We make sure that for every instance of every SAP system which sends data into Sentinel, we have the value of 'no'- which means all trusted and trustee RFC connections have been migrated as per SAP note 3089413. This alert rule will produce an incident with a severity level of high for every system which is not protected, with the exception of a system which is undergoing a migration and provides a value of 'client' for parameter 'rfc/allowoldticket4tt'. Systems which are in the process of being migrated will create an incident of medium severity.
Prerequisites:
- Make sure you are running a recent version of the Microsoft Sentinel Solution for SAP® applications.
- Check if you have entries for PAHI table coming in from each of the relevant SAP systems. Note that PAHI table is loaded from SAP on a daily basis. If PAHI entries are missing for any of the SAP systems you have, consider SAP note 1733253 recommended actions and verify that your systemconfig.ini file has PAHI_FULL = True see examples here.
SAP - (Preview) New trusted RFC connection [capture-replay vulnerability in SAP NetWeaver CVE-2023-0014]
One important recommendation of the FAQ for Security Note 3089413 is to activate table logging for table RFCSYSACL and periodically check for newly added trusted connections.
This alert rule detects a successful addition of a trusted RFC connection to an SAP system by continuously listening for changes to tables RFCSYSACL and RFCTRUST which document the trusted RFC communications allowed, in near real time.
Prerequisites
- Make sure you are running a recent version of the Microsoft Sentinel Solution for SAP® applications.
- Table logging is set for tables RFCSYSACL and RFCTRUST (this should be on by default) in your entire SAP landscape.
- The Sentinel agent is configured to ingest table changes from table DBTABLOG (ABAPTableDataLog = True ) see examples here
Learn More
Microsoft is committed to empowering our customers with security tools and platforms to enable critical protection for your organization and users. To learn more about Microsoft Sentinel solution for SAP please refer to:
- Microsoft Sentinel solution for SAP offer
- Microsoft Sentinel Pricing
- Demo
- SAP deployment guide
- MSIT case study
- AKS high availability guide for the SAP connector agent
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.