- Home
- Security, Compliance, and Identity
- Microsoft Sentinel Blog
- RSAC 2023: Microsoft Sentinel empowering the SOC with next-gen SIEM
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
With an increase in the number and severity of cyberattacks over the years, security remains a significant challenge. It is paramount for organizations to enhance their security posture and defend against cyber threats with end-to-end visibility across their hybrid environments. Microsoft Sentinel is a next-gen SIEM powered by the cloud and AI, with a deep understanding of the threat landscape, enabling defenders to proactively hunt and mitigate threats in real-time.
To provide customers with a comprehensive and integrated security solution, Microsoft Sentinel harnesses the strong and growing ecosystem of security solution providers, managed security service providers (MSSPs) and community members. Our ecosystem delivers differentiated security solutions, managed services, and other content to help our mutual customers protect their multi-cloud, multi-platform business.
This year at the RSA Conference in San Francisco, we are excited to:
- Announce Workspace Manager, a new capability to manage multiple workspaces at scale.
- Announce upcoming Hunts capability for security operations to manage end-to-end hunting use cases.
- Share our strategy to leverage out-of-the-box (OOTB) content to address your unique security use-cases and introduce new domain-centric solutions powered by Advanced Security Information Model (ASIM) for optimal OOTB content value.
We look forward to showcasing our vision and innovations and hearing directly from customers and partners in the Microsoft booth 6044 at the North Expo. Join us to learn more about our announcements and more.
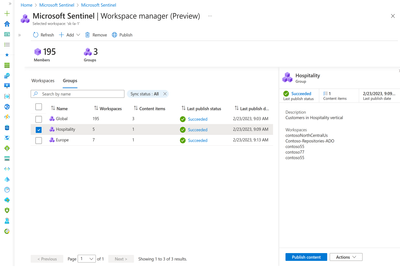
Workspace Manager
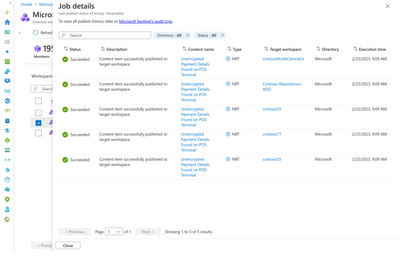
We are excited to announce the public preview of Microsoft Sentinel's Workspace Manager enabling large enterprises, MSSPs and MDRs to manage multiple Microsoft Sentinel workspaces at scale from a central point. Workspace Manager supports multi-tenant scenarios for customers with Azure Lighthouse enabled.
As enterprises expand globally, they have distributed workloads, increasing data residency requirements that might lead to multi-workspace and multi-tenant Microsoft Sentinel deployments. The ability to operate across multiple Microsoft Sentinel workspaces can be useful for MSSPs and large organizations managing security for multiple clients or tenants.
The flexibility of operating across multiple workspaces invariably results in management complexity, especially when it comes to SIEM content. Without central control and visibility, it can be time consuming and challenging to operate a scalable and consistent distributed setup.
Groups allow you to organize workspaces together based on business groups, verticals, geography, etc. These groups can be paired with a set of relevant content items like workbooks, analytics rules, automation rules and more - allowing users to centrally configure and distribute content across workspaces.
This builds on the workspace management capabilities for SAP, currently in public preview. The Microsoft Sentinel solution for SAP® applications provides SAP management teams visibility into SAP business applications across multiple workspaces providing security insights. Security teams can permission SAP teams to access security data strictly for those applications, allowing for deeper collaboration across teams while minimizing what data is shared.
Hunts
Proactive threat hunting is a process by which security analysts seek out undetected threats and malicious behaviors by creating a hypothesis, searching through data, validating that hypothesis, and acting when applicable. Actions can include creating new detections, threat intelligence, or incidents. With the upcoming public preview in May 2023 of the new “Hunts” feature we are providing a first step towards an end-to-end hunting experience within Microsoft Sentinel by allowing customers to keep track of new, active, and closed hunts in one place.
Within Hunts security analysts can proactively hunt threats based on specific MITRE techniques, potentially malicious activity, recent threats, or their own customer defined hypothesis. They can use security-researcher-generated hunting queries, custom hunting queries, or bookmarks.
Now, customers can collect evidence, investigate entities, annotate their findings, and share them with their teams using hunt specific bookmarks all in one screen. Once threats are found in the hunts tab, customers can create hypotheses and act on results by creating new analytic rules, new incidents, new threat indicators, and running playbooks.
Discover and leverage OOTB content to address your unique security use-cases
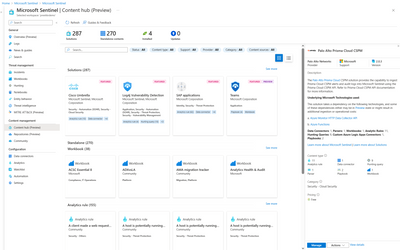
Microsoft Sentinel OOTB content and solutions allow customers to easily discover and manage packaged solutions for end-to-end security operations center (SOC) scenarios based on products, domains, or industry. Earlier this year, we announced bulk content management and support for standalone OOTB content in Microsoft Sentinel content hub. As of today, all OOTB content is available for on-demand installation in solutions or standalone content in content hub. We recommend customers to go to content hub to discover any OOTB content. However, some of the OOTB content still exists in various gallery sections of Microsoft Sentinel like analytics templates gallery, workbooks template gallery, etc. By June 2023 we plan to complete OOTB centralization in content hub by retiring the existing OOTB content in Microsoft Sentinel feature galleries. For more details see OOTB content centralization blog and product documentation to help you plan for these changes.
Content hub goes beyond making it easy to discover, deploy and manage content by organizing solutions into packages that include analytics rules, data connectors, hunting queries, parsers, playbooks, workbooks or watchlists. These solutions help security operations (SecOps) teams manage their business from ingesting data, to monitoring security, to detecting issues, to hunting threats, and responding to breaches in a scenario-driven mode with filters to discover content easily for domain categories, content type, support and more.
We categorize OOTB content and solutions into three main groups:
- Product centric: This includes OOTB content and solutions for security products and services for categories like cloud, identity, security, threat intelligence, compliance, network, productivity workloads, DevOps, IOT/OT and more. Additionally, Microsoft Sentinel product specific content also includes SOAR playbooks and SOAR connectors. A few examples include solutions for Azure, AWS, GCP, Salesforce, Vectra, Cisco, ZScaler, ServiceNow, SAP, Teams, Defender for IOT, and more. You can use these solutions to ingest data from the respective providers and leverage analytics, hunting queries, etc. for threat detection and response (TDR) scenarios with the relevant products in Microsoft Sentinel.
- Threat centric: This includes offerings to protect against specific attacks like Log4J, Typhoon (was Nobelium) or Aqua Blizzard (was Actinium), or monitor attack methods across the MITRE framework. This includes a curated set of OOTB content put together by the Microsoft Security researchers to enable you to protect against different threats immediately. Microsoft Security Threat Essentials solution includes a generic set of OOTB detections and hunting queries that helps protect against common threat vectors.
- Domain centric: This includes featured solutions for different domain categories like network, web sessions, audit, user management and more. These domain solutions are product agnostic, hence do not include any data connectors. Instead, domain-centric solutions include analytic rules, hunting queries, and workbooks. The OOTB content included in these solutions is built leveraging the Advanced Security Information Model (ASIM) schema. With ASIM, customers can leverage one piece of content for coverage across multiple products that share the same domain to reduce content management efforts. See Microsoft Sentinel domain-centric solutions to learn more.
We’re happy to announce the new DNS Essentials solution in Public Preview. This solution provides domain centric value for DNS threat scenarios and is ASIM based. This solution provides coverage for 10 different DNS products including Windows DNS, Azure Firewall, Cisco Umbrella, Corelight and more.
The Network Session Essentials solution in Public Preview provides coverage for 15+ different network products that includes Azure Firewall, Palo Alto Firewall, Amazon Virtual Private Cloud and more. A single OOTB detection/analytic rule covers a gamut of different products without having to set similar detections for each product.
We will continue to invest more in domain centric solutions to unlock the capability of delivering more value and coverage for your different threat scenarios with the right set of content.
Strong ecosystem of partners and community members as OOTB content accelerators
Microsoft Sentinel is backed by a rich and growing ecosystem of 350+ security threat hunters who share valuable OOTB content contributions like analytic rules, hunting queries, workbooks, playbooks, notebooks and parsers in the Microsoft Sentinel GitHub repository. Microsoft Sentinel community partners publish product centric solutions that include OOTB content to enable integration of their products and services in Microsoft Sentinel. We’d like to extend our heartfelt gratitude to our community members and partners for their continued partnership in building a powerful security platform for our customers.
Below are some of the recent partner published Microsoft Sentinel solutions that can be discovered on content hub. See the catalog for more details.
- ZScalar ZIA – This is a cloud-to-cloud integration that pushes ZIA logs from ZScalar into Microsoft Sentinel. It leverages the Azure Log Analytics logs ingestion API with Data Collection Rules.
- 42Crunch - 42Crunch Developer-First API Security Platform integration brings 42Crunch logs, alerts, and detections to Sentinel with support for enrichment, investigation, and analysis.
- Cohesity – Cohesity Data Cloud with Microsoft Sentinel integration enables alerting and workflow responses to ransomware incidents.
- Domain Tools Iris – This enrichment solution for Sentinel brings Iris Investigate domain-related attributes to Sentinel investigations, including Risk Score, DNS, Whois, SSL, and more.
- Dynatrace - Dynatrace Software Intelligence Platform for Microsoft Sentinel brings detected Attacks, Vulnerabilities, Audit logs and problem events based on metrics, logs, and traces collected from Dynatrace monitored environments.
- Jamf - The Jamf Protect for Microsoft Sentinel solution creates detailed event data from macOS endpoints into a Microsoft Sentinel workspace in a simple and easy workflow
- NoName - This integration brings NoName Security API protection alerts to Microsoft Sentinel to inform investigations.
- Slashnext - Slashnext URL Threat Analysis and IR for Microsoft Sentinel enables Sentinel with API connection to Slashnext real-time threat intelligence database, continuously updated with the latest phishing threats.
- Talon Cyber Security – Brings logs, alerts, and event data from Talon Cybersecurity’s secure enterprise browser to Microsoft Sentinel.
- Trend Micro Vision One – Integrates Trend Vision One Workbench Alerts and maps the impacted entities for Microsoft Sentinel usage.
- WithSecure - WithSecure Elements integration with Microsoft Sentinel delivers WithSecure events in Common Event Format (CEF) over syslog, enabling search & correlation, alerting and threat intelligence enrichment for each data log.
We encourage you to join the Microsoft Sentinel community of security experts today! Check out the partners opportunity guide to get started as a Microsoft Sentinel partner.
Learn more about our presence at RSA:
Microsoft is committed to empowering our customers and partners with tools and platforms to enable critical protection of users and organizations.
- We are excited to see you all at the Microsoft booth 6044N at RSAC 2023.
- Join us on April 25th, 2023 from 10:10 AM to 10:30 AM for a theater session to learn more about our latest innovations in Microsoft Sentinel and engage with our security experts.
Resources
To learn more about Microsoft Sentinel, see:
- Microsoft Sentinel documentation | Microsoft Learn
- Workspace Manager | Microsoft Learn
- Out-of-the-box (OOTB) content centralization changes - Microsoft Sentinel | Microsoft Learn
- Content Centralization Changes blog.
- Microsoft Sentinel Domain-centric solutions
- Microsoft Customer Stories
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.