- Home
- Security, Compliance, and Identity
- Security, Compliance, and Identity Blog
- Manage the most critical data security risks inside your organization with intelligent automation
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Data security incidents are commonly caused by insider actions, accounting for nearly 35% of all unauthorized incidents*. Even the strongest cybersecurity programs can be undermined by insiders who either intentionally or unintentionally compromise an enterprise. Insider risks such as data leakage and data theft are particularly common, and it has become crucial for all organizations to address, especially in today’s hybrid work environment. Gartner® predicts, “By 2025, insider risk will cause 50% of organizations to adopt formal programs to manage it, up from 10% today.”**.
Combating evolving data security risks requires a concerted effort across the organization to mitigate user error and malfeasance. In fact, Bret Arsenault, Microsoft’s Chief Information Security Officer, recently shared four lessons on managing insider risks within a company in a new Harvard Business Review article, Your Biggest Cybersecurity Risks Could Be Inside Your Organization. He explained how he matured a small internal initiative into a business unit that reports directly to the CEO, emphasizing the importance of proactively managing the risks posed by insiders.
In the article, Arsenault highlighted how using machine learning tools helped his team do more with less and how adaptive security capabilities can detect risky activities and mitigate potential impact while maintaining productivity. Research shows that organizations with fully deployed AI/ML and automation security technologies experienced almost 65.2% less cost compared to those with no AI/ML and automation deployed when a data breach happened***. By combining human expertise with the power of technology, we can work toward a safer, more secure digital future.
With this in mind, we are pleased to announce the public preview of new features to help organizations manage insider risks more effectively by leveraging intelligence through AI/ML and automation:
- Leverage Optical Character Recognition (OCR) to detect insider risks around sensitive data in image formats
- Finetuning insider risk policies with real-time analytics
- Reduce noise with automated email signature exclusion
Microsoft Purview Insider Risk Management correlates various signals to identify potential malicious or inadvertent insider risks, such as IP theft, data leakage, and security violations. Insider Risk Management enables customers to create policies to manage security and compliance. Built with privacy by design, users are pseudonymized by default, and role-based access controls and audit logs are in place to help ensure user-level privacy.
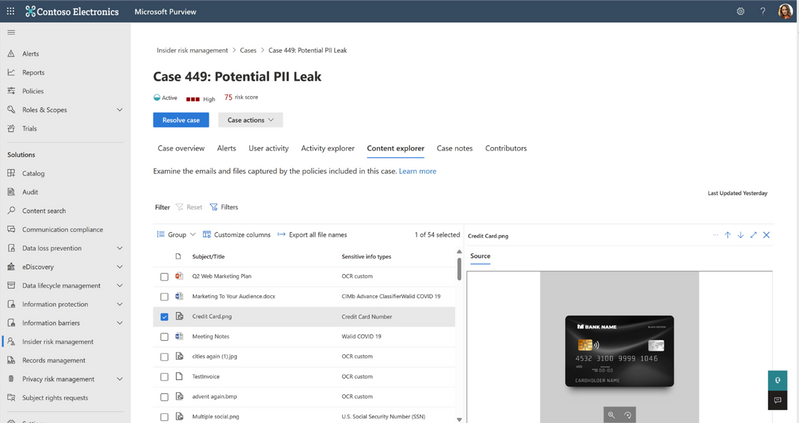
Leverage OCR to detect insider risks around sensitive data in image formats
Sensitive data can take many forms beyond text, including images such as driver's licenses and scanned contracts saved in PDF format. We're pleased to announce that Insider Risk Management now supports the detection of risky activities around images and PDFs containing sensitive data in SharePoint, Teams messages, and endpoints. This is made possible through the AI/ML-powered Optical Character Recognition (OCR) technology, which can extract text from images and PDFs and support over 150 languages. By leveraging OCR, which is also supported in Microsoft Purview Information Protection and Data Loss Prevention, Insider Risk Management can help detect potential data leaks or theft and mitigate the risk of data exfiltration. This announcement underscores our commitment to providing an integrated platform approach to fortifying data security.
Fine-tuning insider risk policies with real-time analytics
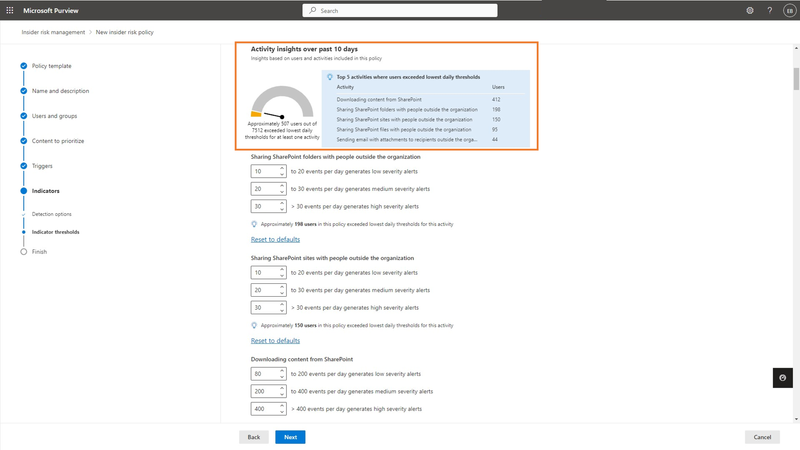
As organizations have varying risk appetites and evolving priorities, detecting insider risks that may lead to a data security incident cannot be a one-size-fits-all approach. Customizing policies is essential but fine-tuning them can be a frustrating and time-consuming task. Typically, admins have to wait for several days to see if the policy works as expected.
With a new update set to roll out in the next few weeks, admins can leverage real-time analytics in the policy wizard to help predict the number of users that could potentially match a given set of policy conditions. This feature enables admins to quickly adjust the selection of indicators and thresholds of activity occurrence, so they can efficiently translate their insider risk strategies into pragmatic controls. This update is yet another step toward making the process of detecting and mitigating insider risk more efficient for organizations.
Reduce noise with automated email signature exclusion
We understand that noisy alerts can make the investigation process frustrating. In our last blog, we announced the deduplication work for the most common 13 signals, including SharePoint file download, File print, File upload to cloud. In addition to the noise coming from the system itself, another main source of noise is email signatures, which are often detected as attachments in emails, leading to false positives of users trying to send potentially confidential files via email.
We are excited to announce the public preview of the email signature exclusion feature, which will be rolled out in the next few weeks. With this feature, admins will no longer need to manually dismiss alerts that involve email signatures. Once admins opt-in to email signature exclusion in insider risk settings, policies will automatically exclude email signatures as potentially risky activities, improving the accuracy and efficacy of insider risk alerts.

NTT Communications addresses insider risk with Microsoft Purview
Data security is a top priority for many organizations, and NTT Communications Corporation, based in Tokyo, Japan, is no exception. To enhance the protection of its information assets and mitigate evolving threats, NTT Communications adopted a new approach that leverages Microsoft Purview. One of the primary focuses was on improving the transparency of internal risks, which was enabled by Microsoft Purview Insider Risk Management and Microsoft Purview Information Protection.
“We completed our Information Protection and Insider Risk Management deployments thanks to the high affinity of features within the comprehensive package of Microsoft 365 E5. We were successful in achieving satisfactory results within six months after deployment.” – Hideharu Inoue, Information Systems Department Supervising Director, Digital Transformation Promotion Division, NTT Communications Corporation
You can learn more about their story in this article.
Get started with Insider Risk Management today
We are thrilled to share these announcements with you. Here is a summary of next steps and other resources to help you and your organization get started with these capabilities:
- Watch the Microsoft Secure breakout session: Secure data with an intelligent and people-centric approach, where I introduced and demonstrated Adaptive Protection in Microsoft Purview, the new capability that leverages more than 100 built-in and ready-to-use indicators and machine learning models in Insider Risk Management to help understand how users are interacting with data, assign risk levels and automatically tailor DLP controls.
- Learn more about Insider Risk Management in our technical documentation.
- Insider Risk Management is part of the Microsoft Purview suite of solutions designed to help organizations manage, govern and protect their data. If you are an organization using Microsoft 365 E3 and would like to experience Insider Risk and other Purview solutions for yourself, check out our E5 Purview trial.
- If you own Insider Risk Management and are interested in learning more about Insider Risk Management, leveraging Insider Risk Management to understand your environment, or building policies for your organization or investigate potential risky user actions, check out the resources available on our “Become an Insider Risk Management Ninja” resource page.
- Erin Miyake, Principal Product Manager, Microsoft Purview Insider Risk Management
*Insider threat peaks to highest level in Q3 2022
**Gartner, Predicts 2023: Cybersecurity industry focuses on the human deal, Jan 25, 2023
GARTNER is a registered trademark and service mark of Gartner, Inc. and/or its affiliates in the U.S. and internationally and is used herein with permission. All rights reserved.
***Cost of a Data Breach, IBM, 2022
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.